TryHackMe - Gotta Catch'em All! (Beginner)
An easy room with beginner-friendly Crypto challenges.
Welcome to a very quick write up.
Still in the topic of covering the absolute basics. I was initially not going to be writing about this one because I was just going to be doing it for fun, but it showcases some basic cryptography examples that may come in handy for somebody starting their journey.
Find the room for free here: TryHackMe - Gotta Catch’em All!
Reconnaissance
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
SSH and web. We already know the drill, let’s jump straight away to the website to find the SSH creds.
Port 80
Enumeration
A default page is all we find when connecting to port 80. It’s slightly modified, so why not taking a look at the source code?
We find some hard-coded pokemon in a script but it just looks like a red herring. If we keep scrolling down we find this:
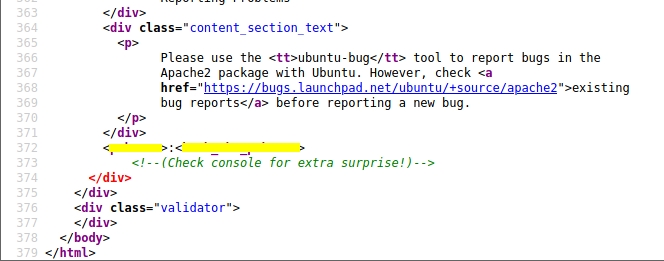
This really looks like a username and password. Why not trying it in port 22?
Port 22
First flag
ssh -l pokemon $ip
So we have 4 flags to find, let’s start doing a quick reckon in the user directory:
ls -R *
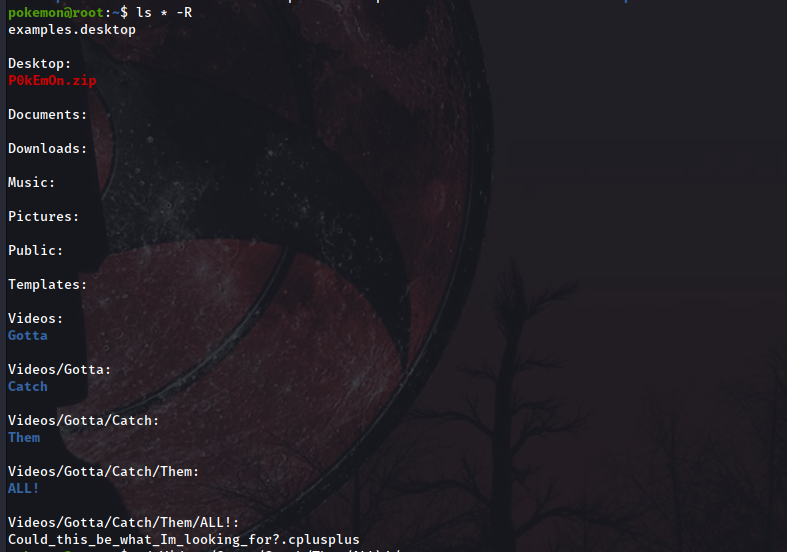
Great, it seems we have found 2 interesting things:
A zip file in /Desktop. If we unzip it we find the first flag. To decode it we will use
xxdand it’s binary manipulation abilities. Passing the flags-r -pwill convert any hexdump data in ASCII characters that we can read.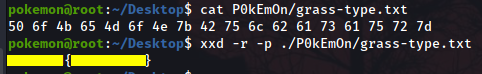
A
C++source code containing new creds. We don’t need them yet so we’ll take a note and move on.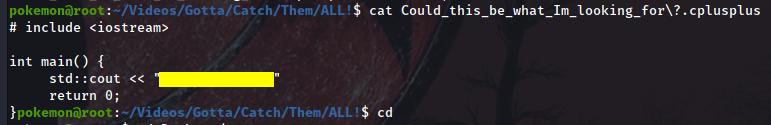
Privesc + Second flag
When we start exploring outside of the home folder of the user we initially found creds for, we stumble across this:
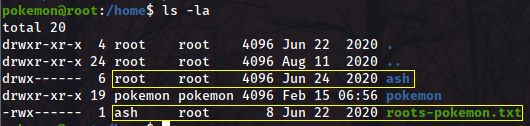
The other user we found creds for is the owner of the file, and the file is in the root group. Looks like it’s time to escalate our privileges. Doing sudo -l with our current user doesn’t bring anything up, so let’s just switch user with su ash
When connecting, something weird happens:
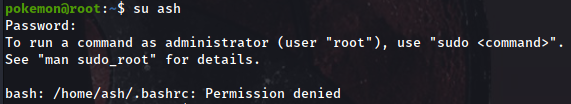
We can’t see the bash history? If he cat /etc/passwd we even see this user hasn’t got a shell defined for them:
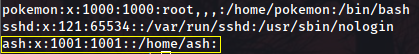
So just let’s try and escalate to sudo. sudo -l reveals we can cast any command we want as sudo
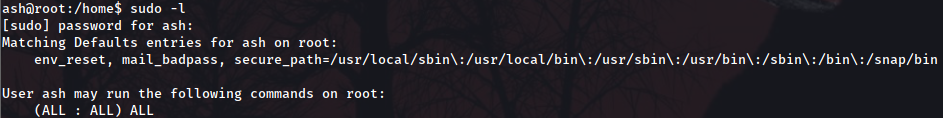
Now, to start the privilege escalation, first thing to do is checking whether we have permissions to doing so from this user with sudo -l:

Let’s go for the easy win: sudo su
Now that we are root we can see the file we mentioned early:
root@root:/home# cat roots-pokemon.txt
<Redacted>
Third and Fourth flags
We saw earlier that the file within the .zip archive was called green-type.txt. Let’s try and take advantage of the naming and try luck by using the find command and some RegEx:
root@root:/home# find / -type f 2>/dev/null | grep -E "type.txt$"
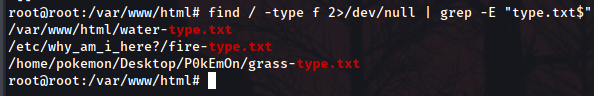
There we have our 2 last flags!
Fire type
Starting with the fire type, we get a base64 encoded string:
root@root:/home/pokemon# cat /etc/why_am_i_here?/fire-type.txt
UDBrM20wbntDaGFybWFuZGVyfQ==
Fortunately for us, Linux has a command which decodes base64 strings for us by calling it directly with the flag -d
root@root:/home/pokemon# base64 -d /etc/why_am_i_here?/fire-type.txt
<Redacted>
Water type
We find ourselves with this:
root@root:/var/www/html# cat water-type.txt
Ecgudfxq_EcGmP{Ecgudfxq}
It looks like a Rot ciphertext. We can now just copy-paste it in any online Rot solver, but I’m going to showcase the tr command and do this from the CLI.
I had a hinge Ecgudfxq meant Squirtle, by the letters distribution and the lack of letters repetition. If we know the first cipher letter E is equivalent to plaintext letter S, our tr command will start with e-z, then from a to the letter before e (a-d) and then we need to repeat it with the capital letters: e-za-dE-ZA-D. Then, we want to translate that into a format we can read, so if e equals s, the first letter we need to put for the command is s to z, then from a to the preceeding letter to s, which is r: s-za-rS-ZA-R. Our command will look like this:
root@root:/var/www/html# cat water-type.txt | tr 'e-za-dE-ZA-D' 's-za-rS-ZA-R'
<Redacted>